This post looks back at the CafePress data breach of 2019, the compromised user data, how CafePress handled the breach, the resulting fall-out, and how consumers and companies can protect themselves from future hacks.
About the CafePress data breach
CafePress is a popular custom T-shirt and merchandise online retailer that was hacked, exposing the email addresses for over 23 million users. Exposed data included names, phone numbers, and physical addresses. According to CafePress, “in a small number of cases” the last four digits of customers’ credit card numbers and credit card expiration dates have also been exposed. Some users claimed that their details were leaked even though they had deleted their accounts.
More concerning than the exposure of personal data, roughly half of the 23 million compromised users had their passwords exposed due to weak, outdated encryption and hashing methods. The remaining half had no compromised passwords because they only used CafePress through third-party applications, such as FaceBook or Amazon.
How CafePress handled the data breach
Although the breach happened in February 2019, CafePress remained silent and did not immediately notify their customers. In fact, they let seven months lapse.
By July 2019, the breach was being openly discussed on Twitter. Troy Hunt of the haveibeenpwned (HIBP) notification service became aware of the breach and solicited the help of Jim Scott, a security researcher specializing in data breaches. Users first became aware of the breach a few weeks later, on August 5, through notifications from Troy Hunt's HIBP service.
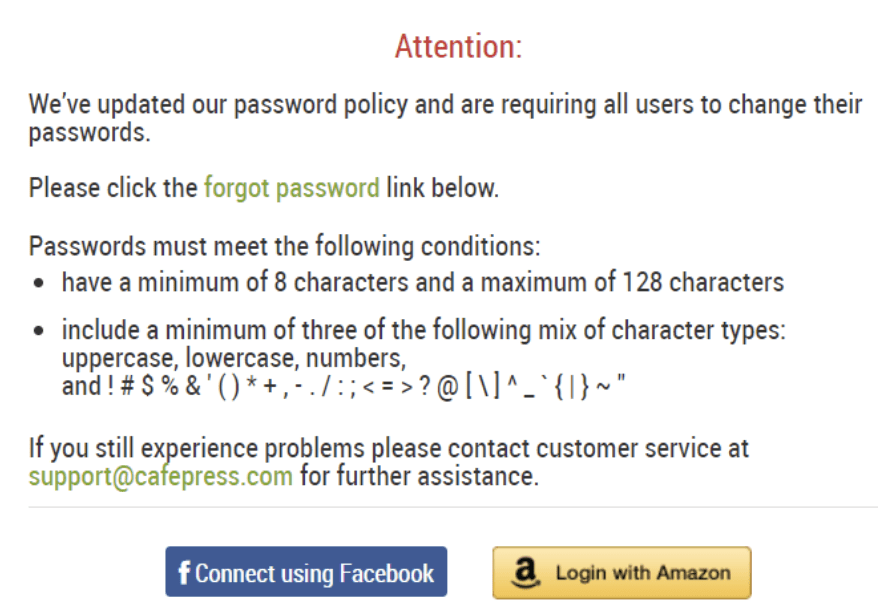
In parallel, on August 5, CafePress forced their customers to reset their passwords under the guise of a security policy change, still without mentioning the breach.
It was not until late September 2019 that CafePress told their customers. Disappointingly, they did not give a complete disclosure of the full extent that customers were exposed.
Once the full details of the breach were exposed, CafePress was hit with a class-action lawsuit and negative press:
"CafePress allegedly relied on Secure Hash Algorithm 1 (SHA-1) as the lynchpin of its data security. Hackers and security experts know that SHA-1 has been useless in protecting data since about 2005. These days, SHA-1 is the digital equivalent of a picket fence when it comes to keeping the wolves from the sheep." Beth Fegan, FeganScott
Lessons learned for both consumers and enterprises
Although the CafePress breach was in 2019, there are still lessons that we can take away from the event for both consumers and enterprises.
Lessons for consumers – own and control your own data
- Speak with your “wallet.” Intentionally buy from those companies who openly share strong security policies.
- Use apassword managerlike 1Password or LastPass to store your passwords securely.
- Do not reuse the same passwords for the same account or across multiple accounts, and do not use simple passwords that can be easily guessed from your social media postings.
- Whenever possible, turn on multi-factor authentication (MFA) for all accounts, and when creating answers for MFA security questions (as noted in point #3) do not use answers that can be easily pulled from your social media postings.
- Minimize the information provided to third parties. Especially avoid giving away Personally Identifiable Information (PII) data like date of birth unless required.
Lessons for enterprises
For enterprises, there are many things that we can learn. These range from how CafePress protected passwords to how they handled their breach. Our takeaways include:
- Show customers that their digital safety is your priority. Have strong policies and controls and state them on your website.
- Disclose breaches to your customers early and in detail to reduce the damage to your brand and to reduce the size of financial penalties from regulators or class-action suits.
- Modernize IAM and API security based on modern best practices including strong password encryption and Multifactor Authentication.
- Use context-aware authorization to ensure that you always know the “who, what, where, when and why” behind every access request before you accept or deny.
Cloudentity is your weapon in the battle against cyberattacks
Cloudentity’s context-aware dynamic authorization platform takes a unique approach to bundling modern IAM and API best practices into lightweight application layers to support rapid and safe application modernization. Our Cloudentity MicroPerimeter™ with CIAM will help you implement MFA, OAuth 2.0, and OIDC to deploy robust identity and enforcement across your enterprise. You can access a free trial or software demo here to experience how this might work for you.
See you on the secure side.
Cloudentity is your weapon in the battle against cyberattacks
Cloudentity’s context-aware dynamic authorization platform takes a unique approach to bundling modern IAM and API best practices into lightweight application layers to support rapid and safe application modernization. Our Cloudentity MicroPerimeter™ with CIAM will help you implement MFA, OAuth 2.0, and OIDC to deploy robust identity and enforcement across your enterprise. You can access a free trial or software demo here to experience how this might work for you.
See you on the secure side.
More news below:
Forbes: CafePress Hacked, 23M Accounts Compromised. Is Yours One Of Them?https://www.forbes.com/sites/daveywinder/2019/08/05/cafepress-hacked-23m-accounts-compromised-is-yours-one-of-them/#79139bed407e
engadget.com: CafePress resets passwords months after reported data breachhttps://www.engadget.com/2019/08/05/cafepress-data-breach/
security affairs: CafePress, the popular T-Shirt and merchandise website, suffered a data breach that exposed the personal details of 23 million of their customers.https://securityaffairs.co/wordpress/89495/data-breach/cafepress-data-breach.html