OAuth and OIDC have become the center point of any API and Identity infrastructure. OAuth2 created a framework allowing every user, device, person, service and thing to support their own distributed means of delegated authorization using a combination of scopes and grants. From smart speakers to connected cars, OAuth and APIs connect everything in the modern world providing a common sinew for interconnectivity and must be secured.
In doing so the industry has put developers into the middle of the security discussion exposing a major shortcoming of legacy IAM providers and API Gateways even while they promote their latest version(s) shouting “future-proof “and “modernization” from the rooftops.
Due to the adoption of the standard and the availability of OAuth clients, the requirements for OAuth servers has changed drastically. No longer are a few simple flows, long lived sessions or opaque tokens sufficient.
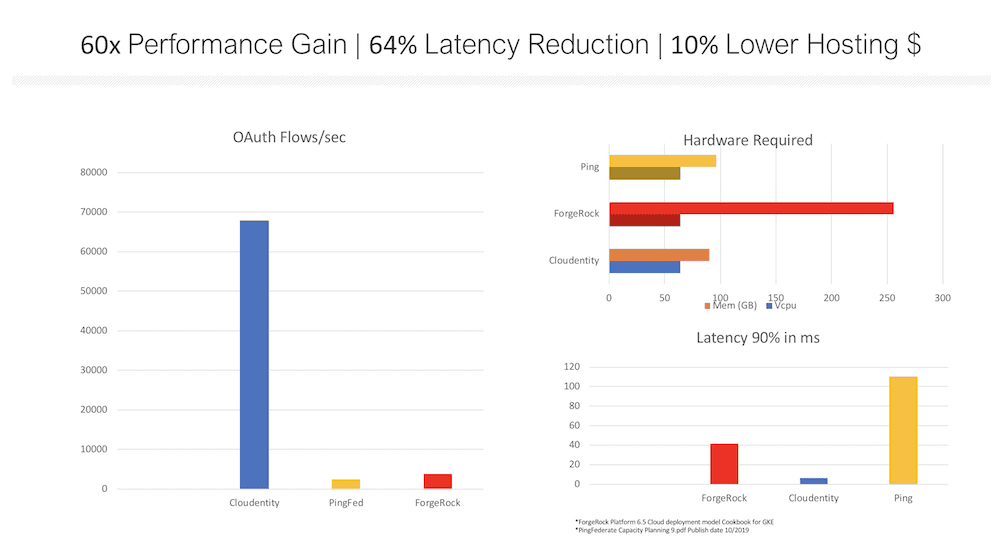
Instead, OAuth servers must: Scale massively.At Cloudentity we’ve had a dozen new customers approach us with OAuth token minting needs ranging from 100,000 flows per second all the way up to a half million and that’s for today’s loads. (Black Friday anyone?)
The monolithic vendors release specs (when they're willing to) that show that, under the most ideal conditions, on their extra-large platforms, under the most ideal scenarios and not running any other functions, 4000 flows per second with significant customer loss generating latency (caused by LDAP, garbage collection and inefficient API calls.)
Provide Multi-TenancyBusinesses are setup to leverage common services with common security mechanisms and standardized methods of approaching authorization and privacy data. Delegated Administration is no longer a nice-to0-have but a must as companies create new platforms for engaging with their partners, customers and even internal business units
Engage Developers to enable DevSecOpsProviding a multi-tenant developer portal is Step One for OAuth service/client onboarding. Other key aspects include a robust set of extensible APIs and microservices to support the services they are building. Then it's important to make their jobs easier by reducing the amount of code they need to create. Offloading authorization, privacy and consent management, sensitive data usage and providing everything in a very succinct “authorization as code” interface gives developers the functions they need to bring products to market faster and more securely without having to learn the intricacies of OAuth, LDAP, SCIM, SAML or compliance requirements like CCPA and GDPR.
Provide Scope and Policy Governance Given the sensitivity of data APIs are moving between businesses, customers and partners and the global regulatory environment, its no longer permissible to allow every development team to build its own solutions. This leads to scope propagation, no understanding how sensitive data flows between APIs or what/when authorization policies are protecting them. Providing real time security and governance updates to the CISO and Data privacy Officer has become a hard requirement and commonizing that across internal and external development teams is the exact reason CIAM.next was built.
The days of compromise in your OAuth and security solutions is over. It’s no longer a decision of whether to shut off security controls, increasing token duration or utilize one-off approaches for managing sensitive data with scopes and grants.
Deploy on our cloud or yoursCIAM.next approached it differently using stateless microservices and APIs to build a multi-cloud authorization control plane. Our goal from its inception was planet scale, simplifying the developer experience, making externalizing authorization and adding governance in a manner that provides distributable identity microservices that work in concert with your distributed apps, APIs, microservices and functions

