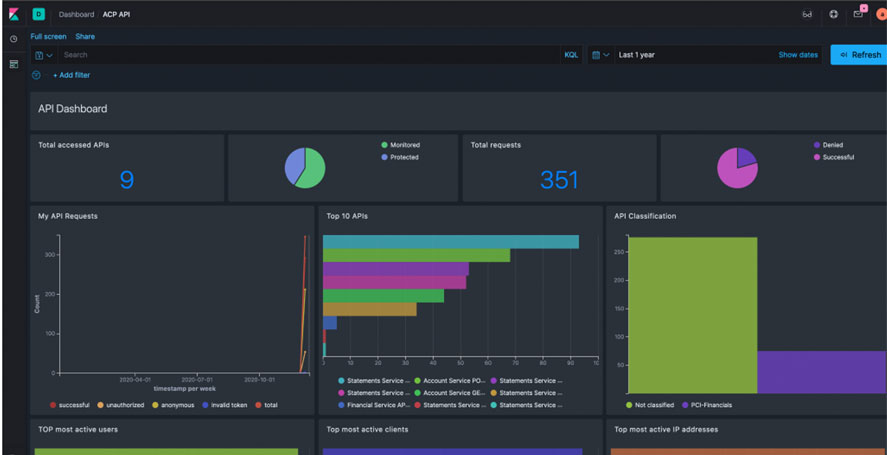
What do CapitalOne, Prestige Software, ManageCartUber, Accenture and the DOD all have in common?
Major breaches through Amazon S3 buckets.
Amazon’s regular security updates in 2017, 2018, 2019 and 2020 have done little to slow the tide of data leaks.
The core problem for S3 is one of authorization both from a scale and a granularity/management perspective. Whether that Authorization is at the root s3 folder or at an individual file, the protections afforded to S3 are rudimentary at best and tied explicitly to AWS Cognito. Enter Cloudentity. In this blog, you’ll learn how to quickly integrate robust Authorization policies that are centrally managed with distributed enforcement to ensure the lowest latency and the highest possible levels of security to your AWS infrastructure leveraging your existing IdP.
The challenge starts by routing s3 traffic through the AWS API Gateway, that allows us to create a CRUD interface to AWS S3. As it turns out, this was much easier than I originally thought. These steps are from the AWS API Gateway documentation, available here, and these instructions are based on those.
Set up IAM permissions for the API to invoke Amazon S3 actions
This is the first step in the process. You need to create a role that will allow API Gateway to invoke S3 actions. By granting specific actions in the IAM policy you create for the role you will enable specific HTTP verbs. For example if I create a role that grants s3:Get* and s3:List* I’l have the rights necessary to support a GET verb. Add an s3:Put* or s3:Post* then I can add or update files.
The last item here is to add a trust policy so API Gateway can call STS:AssumeRole so that API Gateway can assume the role you created. That trust policy must also be attached to this role.
Expose an API method to list the caller's Amazon S3 buckets
In this step you will add your / API endpoints and then add a GET method to that endpoint. This can be done in two ways manually or via a OpenAPI file import. My suggestion is to work through the documentation and set up at least one endpoint and method manually. This will help to understand how the flows work between API Gateway and S3. Once the flow is understood you could choose to use the OpenAPI definition available for download from here to automatically create the entire API. To use this definition, you need to edit the file before you can import it into API Gateway.
Line #7 - "host": "9gn28ca086.execute-api.{region} .amazonaws.com",
Change this to reflect the proper region.
"credentials": "arn:aws:iam::<replaceable>123456789012</replaceable>:role/apigAwsProxyRole",
Change this line to reference the role you created above.
Once you have your REST API created in API Gateway, I recommend that you test it. You can test requests in API Gateway within a Method by clicking on the Test link. For example a quick test of the GET method against / looks like this.
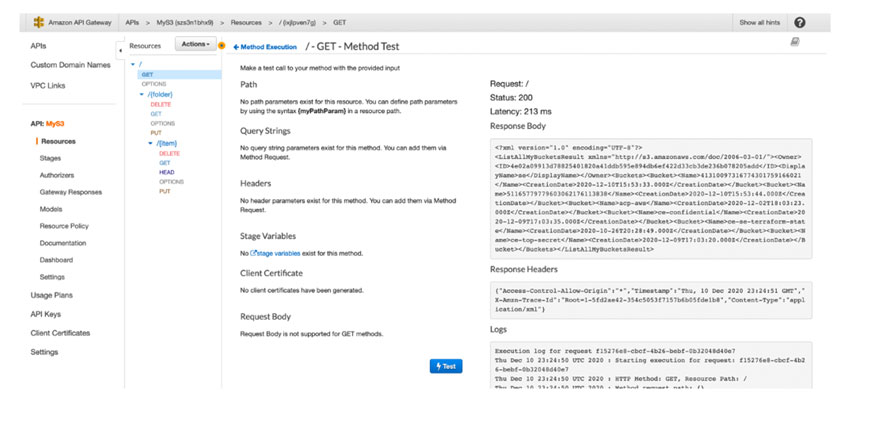
You can see the response body and headers. Once this is complete deploy your API and then use a tool like Postman, to test against the deployed API itself. Once you are happy, then we move into Authorization Control Plane configuration.
Configuring the Authorization Control Plane.
All the instructions to configure ACP to protect the AWS API Gateway are available here.
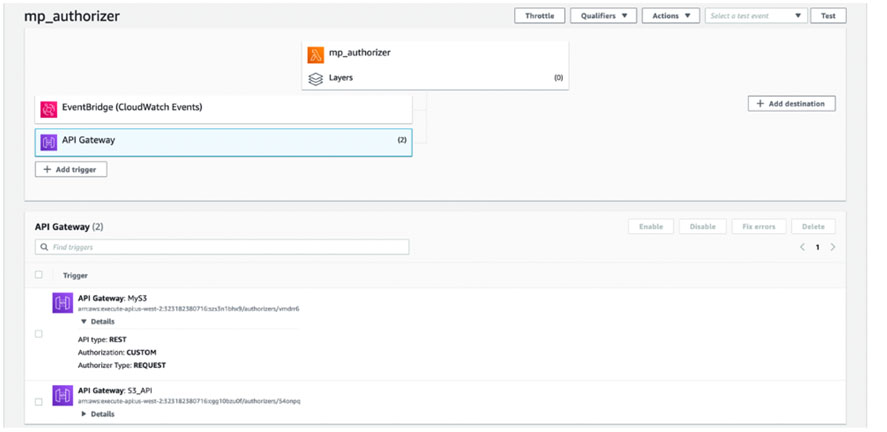
Installing the MP Authorizer Lambda
The first step in the process is to install our MicroPerimeter Authorizer. This software has been packaged as a .zip file that is designed to upload directly into an AWS Lambda function. It performs all Authorization decisions when we are using our new S3 API. The lambda will also log all activity into CloudWatch Logs for review, or bringing into Security Hub or your SIEM.
Please make sure that when you are configuring your lambda you set the necessary environment variables for it to function properly. Those variables are:
ACP_CLIENT_ID
ACP_CLIENT_SECRET
ACP_ISSUER_URL
Configuring Lambda Permissions
You will need to provide permissions to the MP Authorizer Lambda to allow it to call AWS services on your behalf. You need to grant the role that the Lambda is using permissions to API Gateway and Lambda. If you grant:
lambda:*
And
apigateway:*
on all resources then the Lambda will have all necessary rights to function.

Connecting an ACP Service to APIGateway
This step will connect our previous work with the Authorization Control Plane. From APIs / Authorization, simply click Add Gateway API. Once the API that you have constructed is added to the Gateway API. MP Authorizer will start communicating with the API Gateway and introspecting the API’s that are registered for display within ACP.
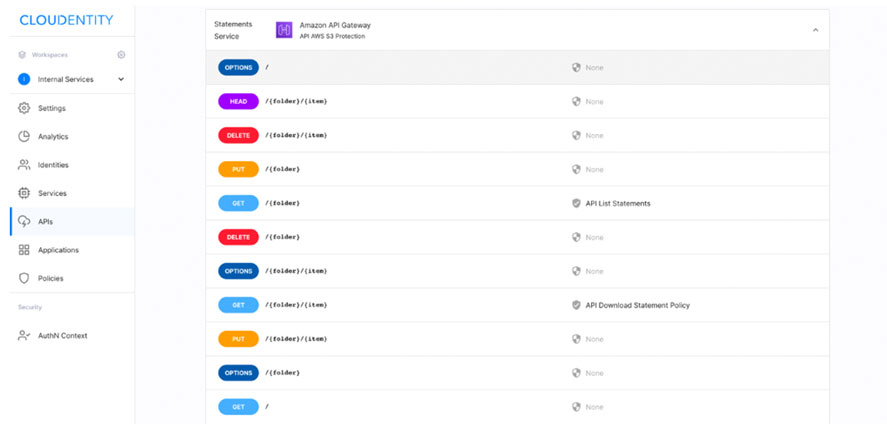
Policies can be applied to individual folders, files and actions on those files, so that you can control how each API endpoint is accessed. For example, you might want to ensure that a user belongs to your IdP’s admin group before you allow them to use a DELETE API call. By applying this policy:
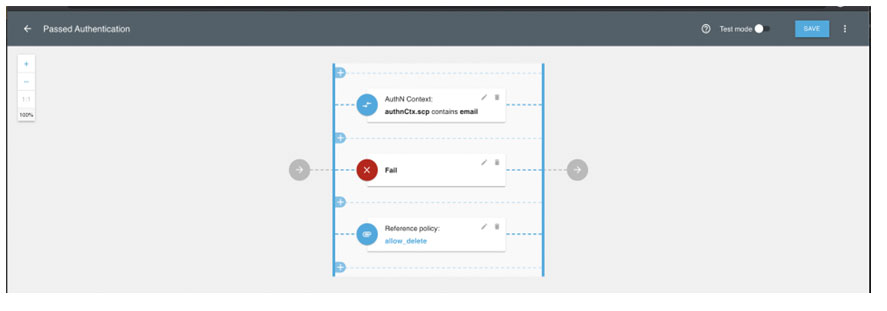
You can easily require a specific group membership.
And lastly is governance and audit of the access and transactions of the S3 buckets