Identity-Aware Authorization at Scale
Authorize API access, enable user consent and data sharing, add fine-grained access control.

Multi-Dimensional Authorization
Add multi-dimensional authorization to your B2B platform using financial-grade OAuth server, distributed API declarative authorization solutions, and Policy-Based Access Control.
Financial-Grade OAuth Authorization Server
Employ multi-tenant authorization server that complies with extended family of OAuth specifications.

Financial-Grade OAuth Server
Multi-tenant OAuth server for SaaS applications with elevated data security and data sharing requirements.

Authorization Server for B2B SaaS Apps
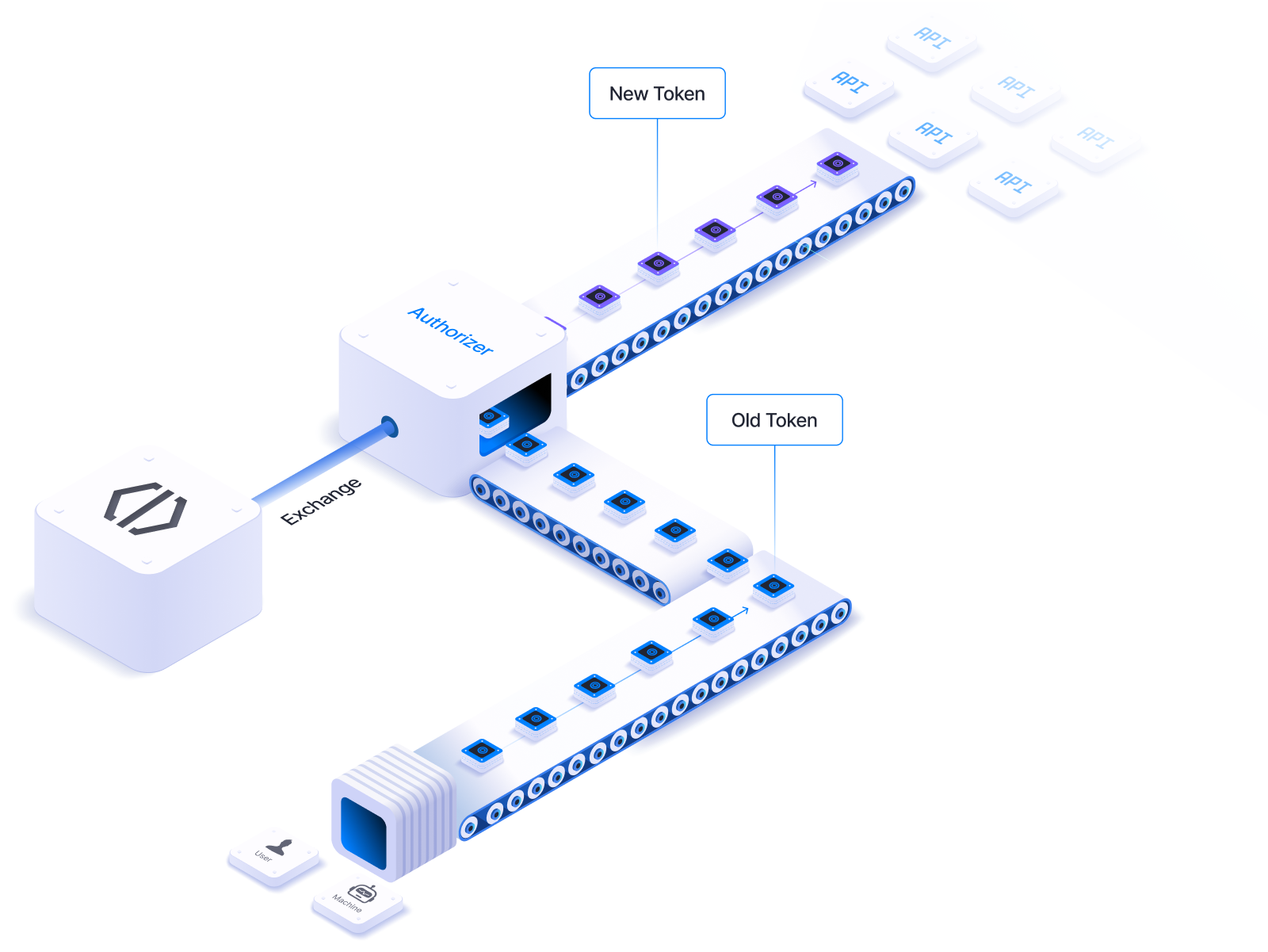
Employ multi-tenant authorization server that replaces a need of a farm of regular servers. Reduce costs, make your architecture simpler, maintain customer isolation.
Create as many authorization servers as you need.
Fine-Grained Authorization and Consent
Empower users to authorize individual transactions. Add fine-grained consent enabling customers to authorize third-party access to discrete resources.
Utilize rich authorization request to make scope of access granular.


FAPI Support, OAuth & OIDC
Extensive support of OAuth & OIDC Open Standards.
One of the most certified for OAuth's financial-grade profiles and a swift achiever of FAPI 2.0 Compliance.
- FAPI 2.0
- Rich Authorization Request
- Token Exchange
- DPoP
- and more...
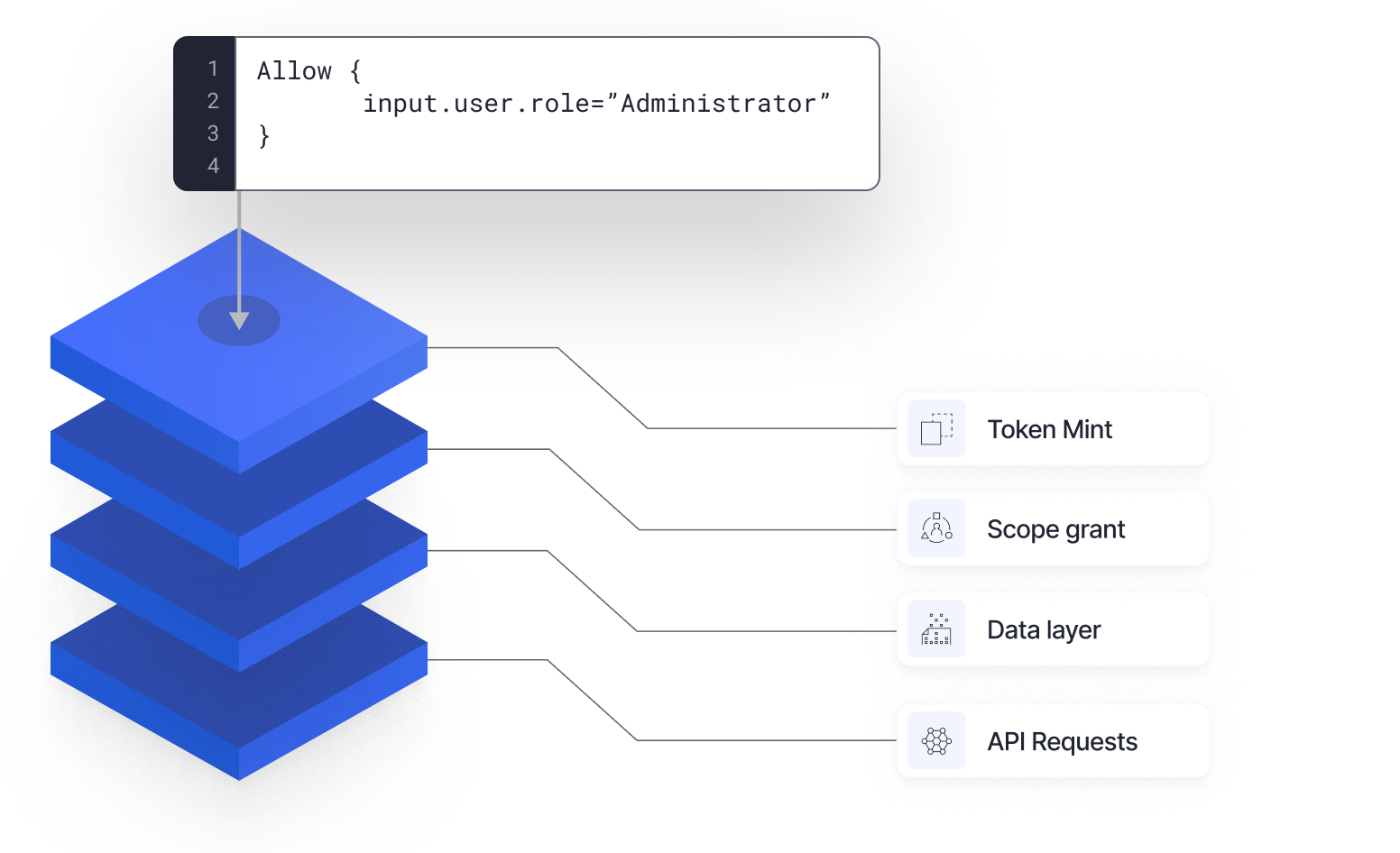
Policy-Based Access Control
Transition authorization from application code to decisive authorization policies for enhanced security, easy modification, and thorough audit. Utilize localized policy decision and enforcement points for millisecond-level latency and automatic policy distribution.
Policy-Based Access Control
Cloudentity enables organizations to apply authorization policies at every application level.
Application Level
Control who can access your application. Enforce MFA, ID-proofing, or permissions.
Token Minting Level
Control which users/machines can get the security tokens. Block token minting for anomalous requests.
Scope Level
Control access to specific scopes. Require MFA for high-value transactions.
API Request Level
Assign policies to APIs for locally enforced, centralized authorization.

Policy Declaration
Enable dynamic access control decisions based on a myriad of attributes like user roles, current location, time of access, the resource being accessed, and much more.
Cloudentity Policies with Visual Editor
Cloudentity’s intuitive built-in visual editor makes policy formulation both flexible and user-friendly, but, at the same time, allows for advanced policy definition.
OPA's REGO Policy Support
Cloudentity contains an embedded REGO policy editor which also includes code samples to help you get started.