Jul 28, 2021
v2.5.0 Highlights
Services, APIs, scopes - now easier to configure than ever - To improve your user experience and provide much more transparency into your authorization perimeter, we have redesigned our views for services and their configuration, APIs, and scopes. You can now enjoy browsing a refreshed Service View that provides you with more information than before. For example, in a matter of seconds you can know which authorizer protects your service. Cool, right? The good news are not finished. You can now configure your services more easily, leverage descriptive hints, and configure scopes in a more convenient way. Don’t forget to take a look at our APIs view, too. It now immediately tells you which type your API is, what method it is, what it path is, which service it belongs to, and by which authorizer it is protected. It shows whether or which policy is assigned to an API.
| Service View | Service Configuration | Scopes | API view |
|---|---|---|---|
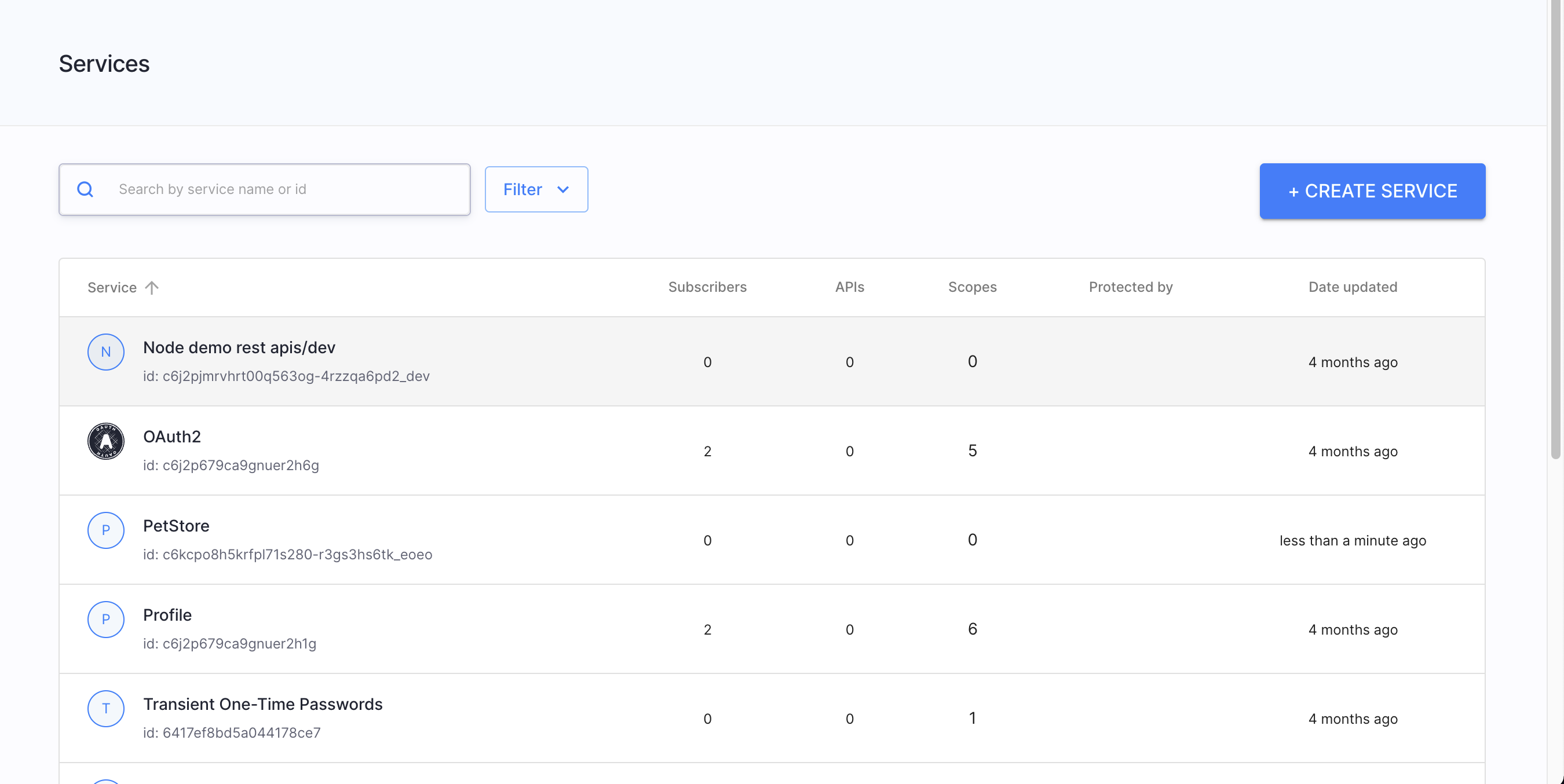 |
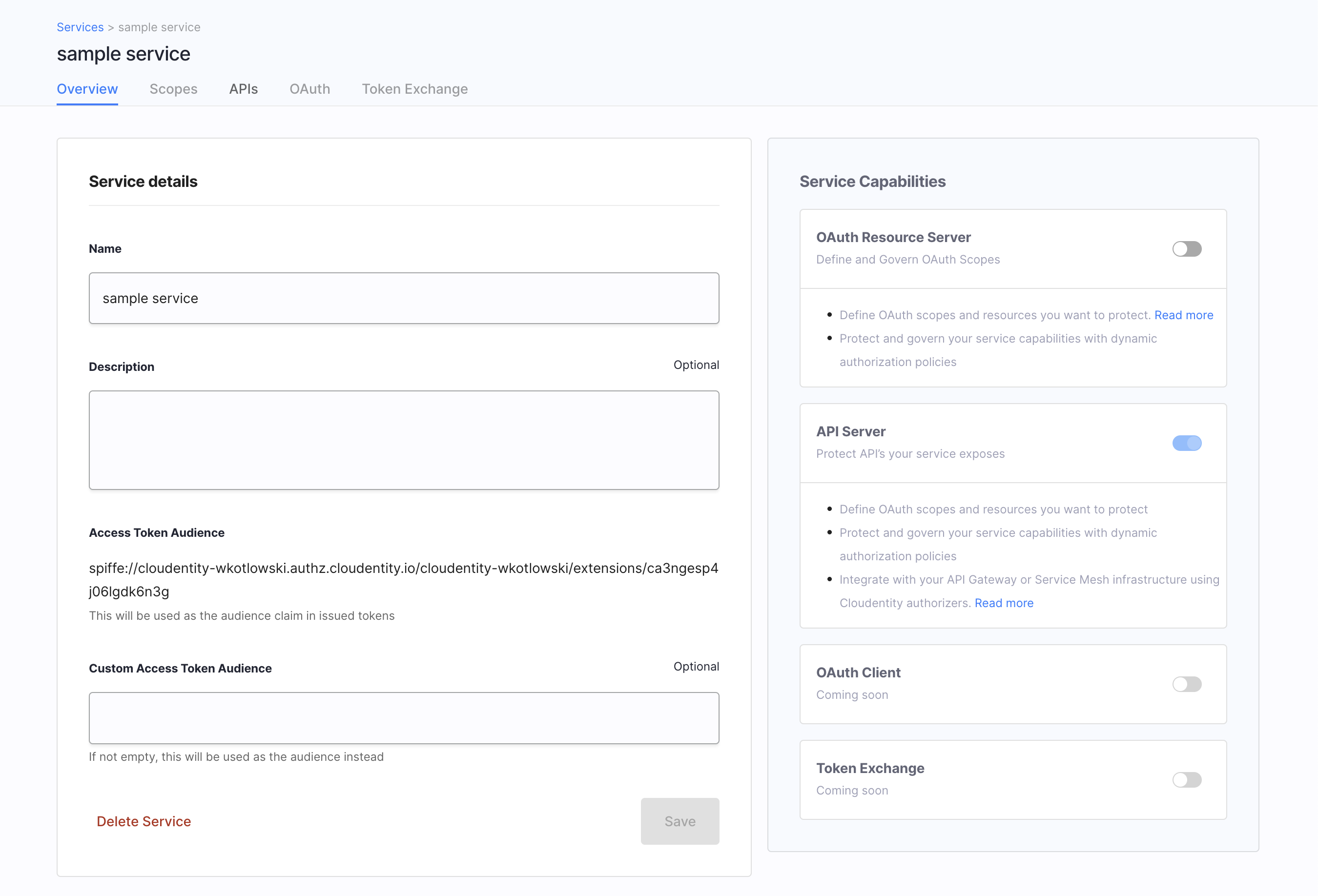 |
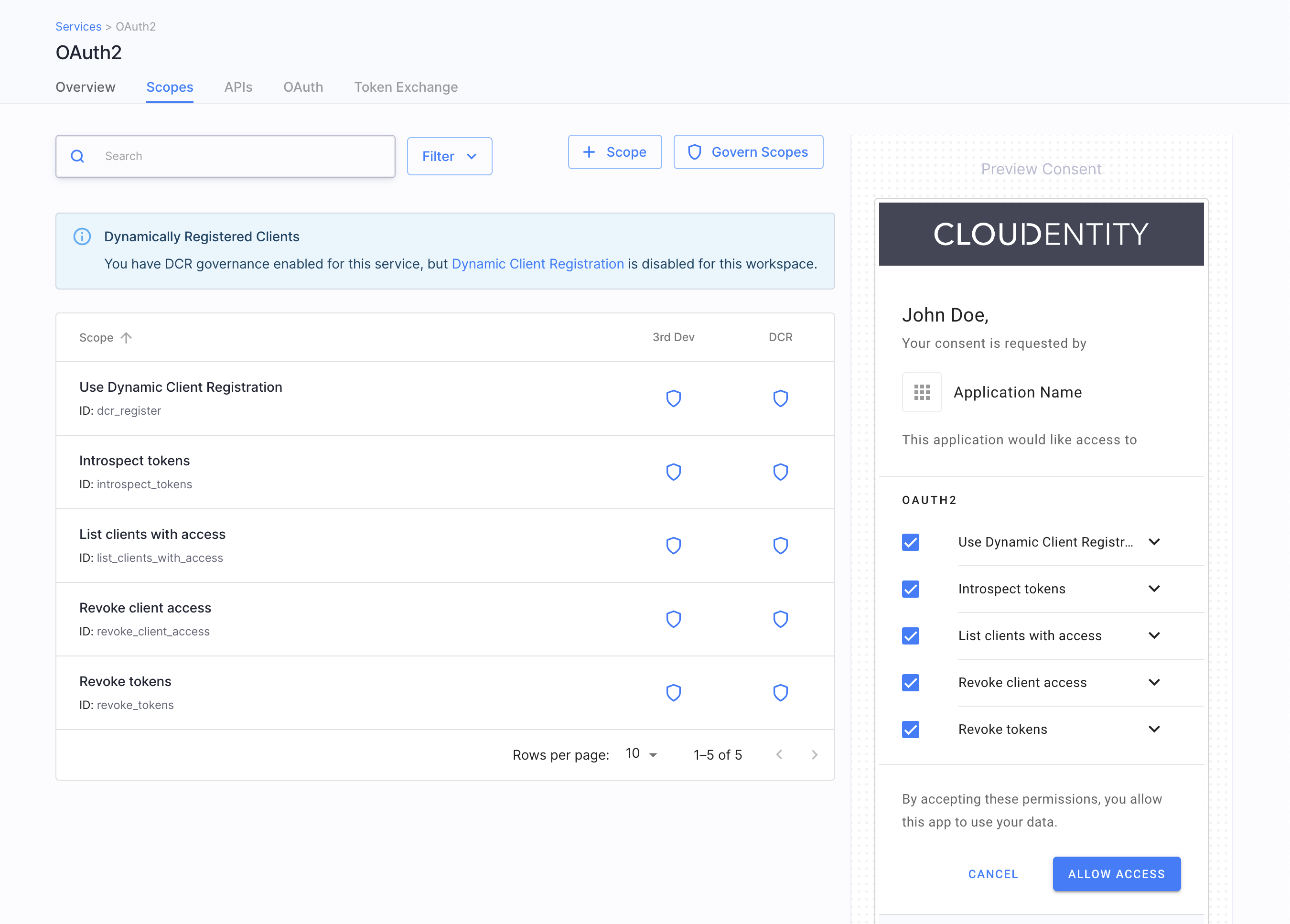 |
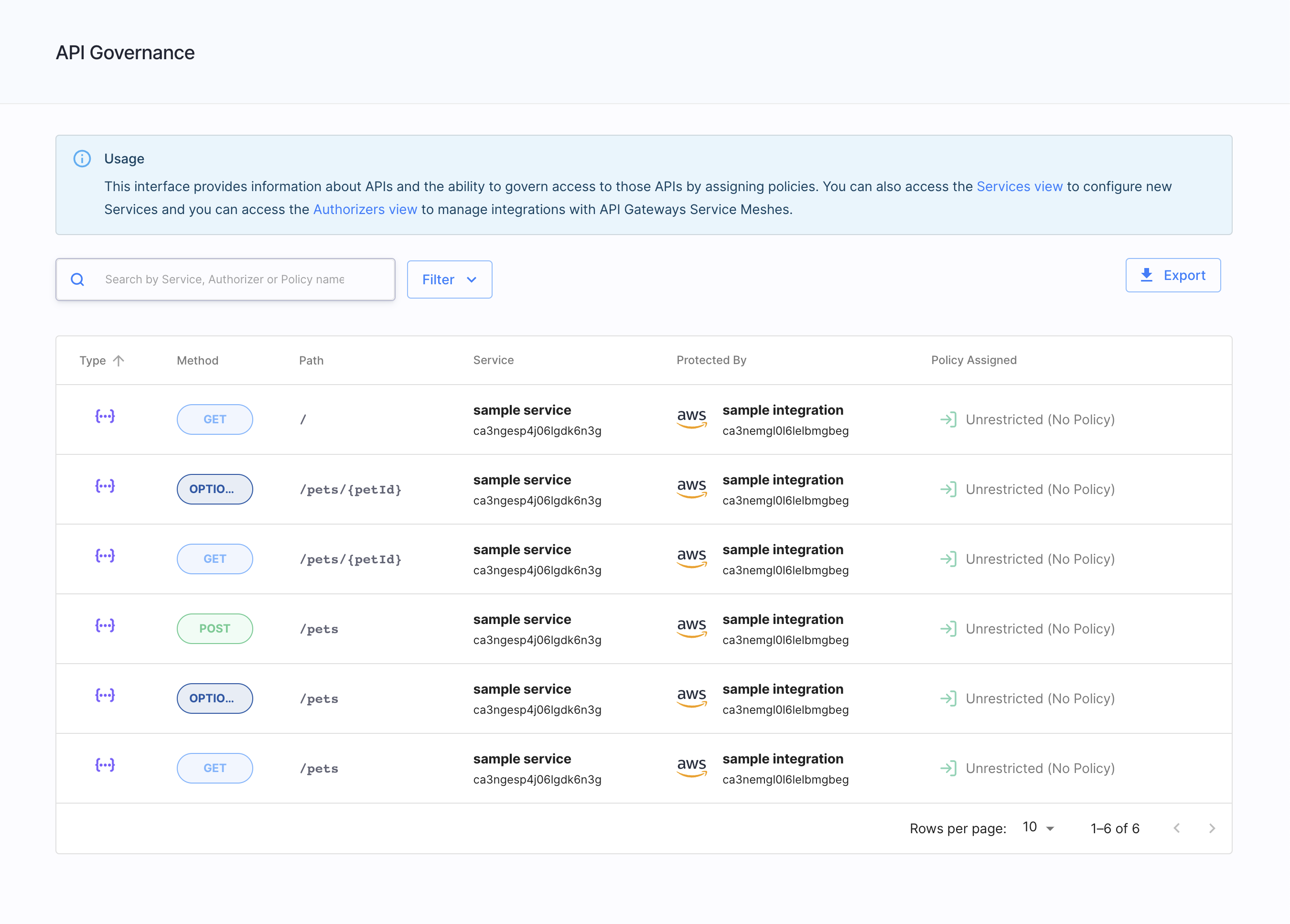 |
Cloudentity on GCP? You’ve heard that right! - If you wanted to add Cloudentity to your infrastructure deployed on Google Cloud Platform, we have good news for you. Check out of brand new Quickstart guide and utilize Google Kubernetes Engine to deploy Cloudentity to GCP!
Major Additions and Changes
[ AUT-5604 ] Service List and Configuration Redesign and Improvement is now finished. For more information, see the highlights section!
[ AUT-6267 ] Client authentication method set to none is blocked when the JWT bearer flow is used.
[ AUT-6387 ] Open Banking Brazil compliant workspaces now have the cpj and cnpj claims
configured by default in the authentication context.
[ AUT-6419 ] A couple of improvements for Policies View:
-
Policy selection dialog component is now caching policies.
-
Current selected policy is displayed always at the beginning of the list with an additional label.
-
New policies are now marked with the New label and displayed at the beginning of the list right after their creation.
-
When no policy is assigned to an API, a label Unrestricted (No Policy) is displayed next to this API.
-
The Save button is now disapled when the user selects a policy that is currently assigned to an API.
[ AUT-6461 ] We have started working on providing support for the delegation flow in the token exchange. Stay tuned!
[ AUT-6473 ] Added a feature flag which blocks access using regular (non vanity domain) domain.
If you wish to block traffic that does not originate from your vanity domain, set the
block_non_vanity_domain_access feature flag to true in your Cloudentity
configuration file.
[ AUT-6574 ] The updated_at field is set for CDR arrangements to the value of the expiry
field whenever the cron job for expired arrangements runs.
[ AUT-6614 ] Cloudentity Authorizers now support the HTTP method REPORT.
Minor enhancements
[ AUT-5944 ] Added an ability to configure brute force protection per type and per tenant.
[ AUT-6238 ] Self registration forms for Identity Pools are now dynamically generated based on the Identity Pool schema.
[ AUT-6297 ] - Added improvements to Cloudentity platform navigation:
-
Audit Events label changed to Logs and now exists as a separate navigation item.
-
Identity Providers now are as a separate navigation items without any parent navigation item.
[ AUT-6450 ] Add an option to download FDX demo package for FDX-compliant workspaces.
[ AUT-6459 ] [Open Banking - FDX] PERSISTENT type consent is created with status EXPIRED instead of ACTIVE.
[ AUT-6606 ] All ID token claims are set for machine grant types
[ AUT-6634 ] Added system-level API to create users for Identity Pools.
[ AUT-6643 ] Removed refresh token limit per subject / client pair.
[ AUT-6727 ] It is now possible to deploy the Standalone Authorizer using Helm Charts!
Bug Fixes
[ AUT-6555 ] Fixed a bug where the updated_at field in the CDR arrangement was not being updated when
calling the revoke by arrangement ID endpoint. The endpoint code has been refactored to use the CDR
repository’s SetRevoked method like the other system revocation endpoints.
[ AUT-6208 ] Fixed the developer portal’s layout in case of multiple added client applications.
[ AUT-6307 ] Fixed validation for adding scopes. It is now not possible to add a scope with ununique name.
[ AUT-6385 ] Refactored the Back to workspace button behavior:
-
After deleting a workspace which was the last visited, the No current workspace information is displayed.
-
Upon entering an URL to a non-existing workspace, the users are now redirected back to the workspace directory or the welcome screen if there is no workspaces.
[ AUT-6416 ] Fixed a bug where for tenant’s with disabled access to Admin and System workspaces, both workspaces would still appear on the workspace list but it would not be possible to access them.
[ AUT-6509 ] Fixing wrong/too extensive imports causing Cannot find module 'ijF0M' error.
[ AUT-6561 ] Fix for resource owner password grant type panic when identity pool is used with invalid password.
[ AUT-6628 ] Fixed bug where new policies were not listed in the Select Policy modal.
[ AUT-6704 ] Fixed a bug where the inline authentication method for the oauth2/revoke endpoint did not
behave like the oauth2/introspect endpoint. We want it to be consistent with introspect so that if
a client has the revoke_tokens scope in its configuration, then it is allowed to revoke other
clients' tokens.
Deprecations
[ AUT-6522 ] Made top-level status field for the Get CDR Consent Request
API deprecated. Instead, the status field from the cdr_arrangement object should be used.
Recommended Database Versions
| Database | Version |
|---|---|
| CockroachDB | 21.2.6 |
| Redis | 6.2.7 |