Selecting Complete Customer Identity Access Management (CIAM) Solution
For managing identity and access for business customers, SaaS applications have several options available to them. They can build their own Customer Identity and Access Management (CIAM) solutions using open-sourced services, utilize standalone identity platforms, or opt for a specialized SaaS platform designed specifically for CIAM. While building a new service not aligned with the company’s core focus can consume significant resources, standalone identity platforms may fall short in terms of access management capabilities and may not be suitable for the needs of business customers. The best option, therefore, is to choose a CIAM SaaS platform that has been specifically designed to integrate with other SaaS applications and meet the demands of business customers.
When selecting the appropriate Customer Identity and Access Management (CIAM) solution for business customers, it’s essential for companies to focus on the tools that offer a comprehensive set of critical features. These features should include efficient business customer onboarding processes, robust handling of business accounts, delegated administration capabilities, and permissions and access control mechanisms. Ensuring that the chosen CIAM solution meets these requirements will ensure a seamless and secure experience for business customers.
Business Customer Onboarding
The CIAM solution you choose should have streamlined and secure onboarding process for business customers. Organization should be able to reflect their structure. Your administrators or your business customers must be able to set up the business organization within the system you choose. Consider the level of customization and flexibility the CIAM solution offers for setting the organization structure and defining access roles and permissions. Even when the CIAM platform offers a registration page, you may want to build one yourself. Think about your branding, all you need are APIs!
Identity Management
The solution’s capabilities for managing business customer accounts including the ability to securely manage and store user information (user registration, login, profile management, password reset, and more).
Delegated Administration
Decide who can be the administrator for the SaaS platform you develop and who can access its particular features. Companies may want to delegate user administration and management to partner employees or administrators from their business customers. Your organization may want to integrate over APIs with the CIAM platform to enhance their SaaS platform with user management capabilities.
Access Control
This refers to the ability to control access to your company resources both in coarse-grained and fine-grained access control methods. For example, access can be controlled based on user roles and permissions. This includes the ability to define and manage user roles, and to restrict access to sensitive information based on these roles. Additionally, not all businesses customers share the same subscription plan. With fine-grained authorization, you can adjust the feature availability to your pricing.
Other Important Features of Best CIAM Solutions
-
Scalability - ensure that the CIAM solution is scalable to meet the growing needs of your business and its customers.
-
Security - provides robust security measures, such as encryption, secure data storage, and regular security audits.
-
User Experience - offers a user-friendly interface and provides a seamless user experience across all devices and channels.
-
Performance and Availability - offers high performance and reliability, with built-in redundancy and failover capabilities to ensure continuous availability.
Manage Business Customer Identities and Access with Cloudentity
Cloudentity provides Identity, Authorization and Consent for today’s most challenging CIAM use-cases. Achieve fine-grained API access control, accommodate massive bursts of scale, delegate access control across partner ecosystems, and much more! Cloudentity offers the industry’s most complete and effective next-generation CIAM platform.
-
Onboard Business Customers - enable your business customers with streamlined and secure onboarding capabilities. Integrate with Cloudentity APIs to create a registration process (both for users and organizations) rich in features and tailored to your needs!
-
Manage Identities - allow your users to self-manage their accounts, set up password policies, control user registration and login process, and much more!
-
Delegate Administration - delegate administrative tasks to other users or groups within an organization. This allows for more efficient management of customer identities, as different parts of an organization can have different levels of access to the customer data they need.
-
Control Who Has Access to Your Platform Resources - restrict who has access to your platform resources and under which conditions they can access those resources. Set up both coarse- and fine-grained access control perimeter around your product to ensure platform’s security!
-
Bring Your Own Identity Provider - Cloudentity supports Identity Federation. We believe that every business should be able to configure multiple IDPs for their customers and partners to avoid proliferation of credentials, for enhanced security, and simply for the users' conveniance. No partner or customer should be made to switch to a different identity provider and migrate their users for the sole integration purpose.
-
Brand Login, Registration, and Consent Pages, and More! - Cloudentity allows you to customize the look and feel of the pages you receive out-of-the-box.
You can, for example, use Cloudentity Identity Pool brandable sign-in page, but choose to build your own user sign-up page using Cloudentity Identity Pool APIs.
-
Do Not Worry About Scale - With Cloudentity, you don’t have to worry about scaling your infrastructure. Our platform is designed to handle hyperscale and can easily accommodate peak loads without any issues. Whether you’re experiencing high traffic or increased usage, our infrastructure autoscales to meet your needs.
In addition to our scalable infrastructure, Cloudentity Identity Pools are built to handle massive scale without compromising on performance. Our lightweight design ensures that you can use our identity pools at any scale without experiencing any performance issues. With Cloudentity, you can rest assured that your platform will continue to perform flawlessly, even as your user base grows.
Set Up Streamlined and Secure Business Customer Onboarding
When using Cloudentity as your CIAM platform:
-
You can utilize Cloudentity Identity Pools to store and manage business customers (users).
-
You can start registering users a couple of minutes after creating a Cloudentity tenant and creating an Identity Pool!
-
You can define custom business customer schemas – parameters used to describe the users – to tailor the customer entity to the needs of your platform and business customer organizations.
-
The multitenancy model of Cloudentity empowers you to easily create multiple workspaces, each representing a distinct business customer organization in CIAM. With this feature, you can configure different identity sources, applications, and permission systems, all within a single Cloudentity Platform tenant, enabling you to efficiently manage multiple customer organizations.
-
You can enable the business customers to set up their organizations or you can do it for them. All using Cloudentity APIs or UI.
For example, you can integrate SaaS platform with Cloudentity APIs and create an organization setup page within your service. Your business customers could then create their organization (a workspace in Cloudentity) with a single click. In the backend, you would just need to call our API. Then, the customer could define different roles they have within their organization and you could just modify the customer schema as needed – again using Cloudentity APIs.
-
You can use out-of-the-box provided and brandable sign up & sign in pages.
-
You can develop your own business customer sign up page using Cloudentity APIs. You can tailor it exactly to your needs, define your customer identity schema, and either register the users yourself or allow them to self-register.
Manage Business Customer Identities
Cloudentity SaaS Platform is designed to provide a secure and convenient way for customers to access online your services and resources, while also providing organizations with a way to manage customer identities and collect valuable customer data.
In CIAM, the focus is on providing a seamless user experience for customers while ensuring security and compliance. Cloudentity platform includes features such as:
-
The Identity Pools design enables you to create multiple pools to segment your user population based on specific use cases.
For instance, you can create distinct pools for vendors, distributors, partners, and employees, among others. This approach allows for greater flexibility and control over access and permissions for each user group, making it easier to manage and secure your platform.
-
At Cloudentity, we believe that every business should be able to configure multiple IDPs for their customers and partners to avoid proliferation of credentials, for enhanced security, and simply for the users' conveniance. No partner or customer should be made to switch to a different identity provider and migrate their users for the sole integration purpose.
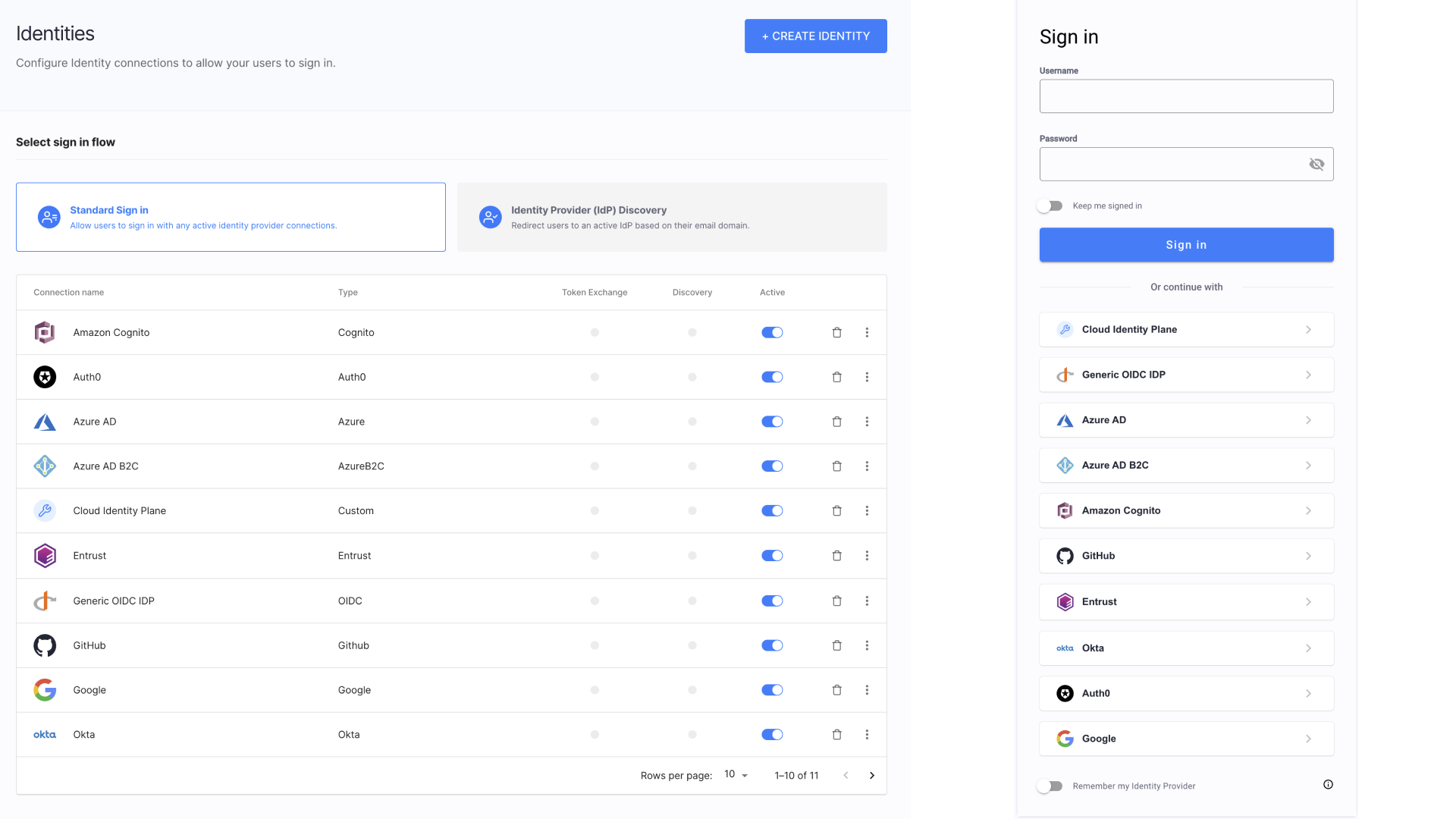
With Cloudentity, you have a possibility to integrate the platform with multiple partner’s or customer’s existing identity and authentication providers using open standards such as OpenID Connect and SAML.
-
User authentication features such as:
-
Passwordless authentication support using Passkey instead of relying on passwords
-
You can easily integrate with user self-service APIs to enable your users to manage their profiles/attributes.
-
Administrator users can assign roles, permissions, and other metadata attributes to users.
-
You can easily query and filter users using Identity Pools APIs.
-
Enhance authentication context with risk information or business information about the user pulled from external services information like subscription plans or licensing.
-
and more!
Consent Management
Consent management is a critical but often overlooked aspect of CIAM. When an application requires access to a user’s data, it must first obtain the user’s authorization. Properly managing user consent can help ensure compliance with privacy regulations and build trust with users.
Cloudentity delivers robust consent management capabilities, including consent page (application) that gathers customer consent, consent self-service portal where users can manage their consents (for example, revoke one at any given time to stop sharing their data), consent admin portal where admin users can manage customer’s consents on their behalf.
Delegate Administration
Delegated administration in CIAM refers to the ability to delegate administrative tasks to other users or groups within an organization. This allows for more efficient management of customer identities, as different parts of an organization can have different levels of access to the customer data they need.
Delegated administration can be used to give different teams or departments within an organization specific permissions to manage and access customer identities, such as managing user accounts, resetting passwords, or modifying user profiles. This can be especially useful for larger organizations where there are many employees who need access to customer data, but not all employees require the same level of access.
With Cloudentity, you can use delegated administration features to assign different roles and permissions for administrator users in the Cloudentity platform to limit access to specific workspaces (or organizations), specific settings in the platform, or applications.
Control Access
Once you have your partners' and customer’s Identities set up, it is time to apply access control. With Cloudentity and its features your job will be much easier. We believe that it is best to use specialized products created with their core responsibility constantly in mind and, in our case, this is authorization and access management.
-
We provide OAuth 2.0 authorization servers that can comply with various security frameworks (like Financial Grade API) and Open Banking requirements.
-
Cloudentity is shipped with built-in multitenancy. We use the concept of workspaces that contain an authorization server and integrated identities and authorizers. It is possible to add multiple workspaces of various profiles within a tenant.
You can have separate workspaces for development, testing, and production environments or create separate workspaces for partners and customers. For example, you can create a workspace for each customers` organization.
-
Our authorization servers support various OAuth and OIDC authorization grant types and client authentication methods.
-
-
Coarse and fine-grained authorization can be easily set up to tailor the final access control measures exactly to the business requirements.
-
Cloudentity supports various authorization models like RBAC (Role Based Access Control), ABAC (Attribute Based Access Control), RISK Adaptive (Adaptable) Access Control (RADAC), or PBAC (Policy Based Access Control) to allow choosing most suitable method for every component of the system.
-
Access can be controlled at any level: organization, service (feature), resource.
-
-
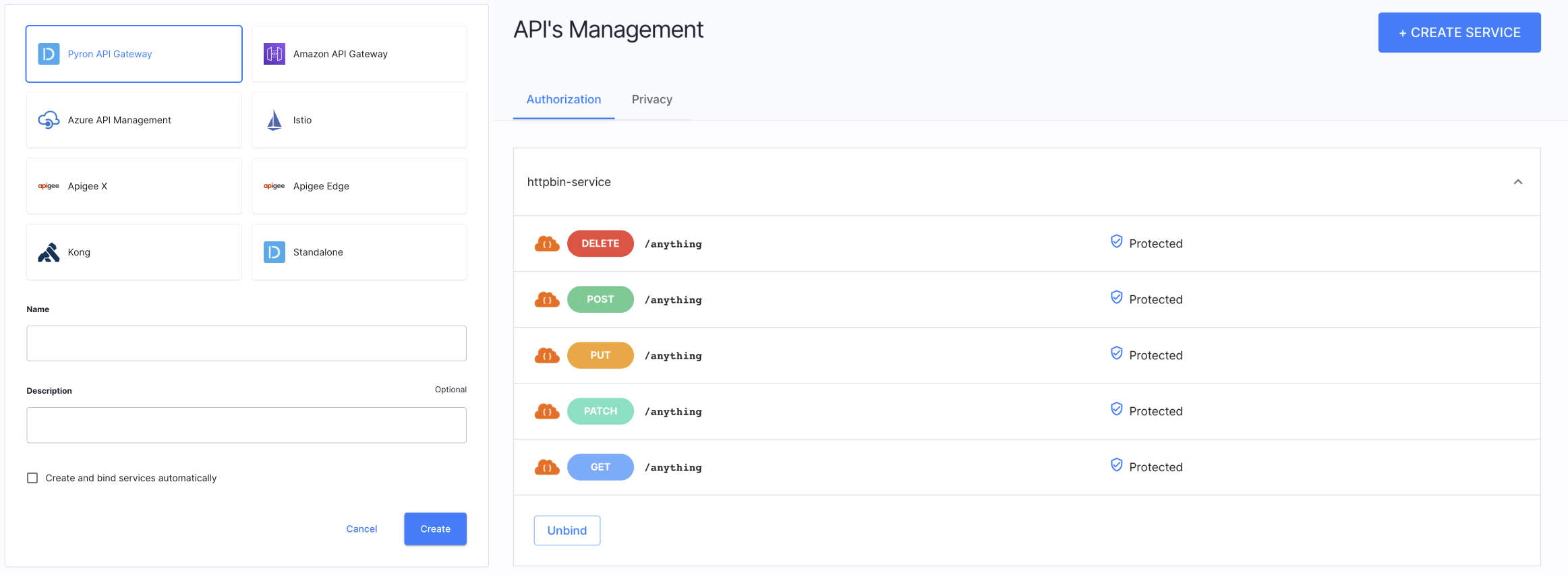
For protecting your applications and APIs, Cloudentity provides Authorizers which our built in-house deployable integration points for major major API gateways and Service Meshes.
Authorizers allow Cloudentity platform to fetch APIs and services from the gateway/service mesh so that it is possible to assign authorization policies and enforce access control.
-
Policies are the key to protecting applications and services with Cloudentity. Cloudentity offers several use-case specific policy types, which can be defined either in the native Cloudentity policy engine or using the Rego standard.
Policies can be applied on both application and service/API level. One non-obvious use-case for policies could be subscription management for end users, where features are enabled based on the claims issued to the application by Cloudentity.
-
We provide a developer portal functionality that allows the developers to register and manage their client applications. Additionally, applications can be dynamically registered with the use of Cloudentity APIs.
-
For partnership and customer enablement, you can use the Token Exchange grant type or use third-party access tokens for access control.
Pick Your Style - SaaS vs non SaaS
Cloudentity provides highly available SaaS regions across the globe, so you can access our solution anytime and from anywhere without any disruptions. We take care of hosting and deployments, so you can focus on using our product.
If you prefer to host the solution yourself, we offer the same binary and tools that we use to run our SaaS infrastructure to your DevOps team. This allows your team to implement our high-scale solution on the infrastructure of your choice. Read about all the offered deployment models.
Why Cloudentity and Not Any Different CIAM Platform

The Cloudentity platform offers unique solutions and capabilities that set us apart from other platforms and authorization servers. It’s important to understand the differences in our approach, as it ensures a robust CIAM (Customer Identity and Access Management) solution for your business needs.
We take a comprehensive approach to CIAM, combining advanced security features with user-friendly interfaces to deliver a seamless experience for both you and your customers. Our platform offers customizable features that cater to the specific needs of your business, enabling you to manage customer identities and access with ease.
Cloudentity conforms to the most demanding standards,including OAuth, Open Finance, FAPI, and other open specifications, as well as holding certifications for compliance. If you need support for a new specification, let us know. We will analyze it and either confirm that we already comply with it or add it to our roadmap.
Our platform is highly flexible, easily adaptable to any CIAM for B2B scenario with a little bit of thought. With our multitenancy model, you can add as many organizations (workspaces) as needed, without worrying about overlaps or risk.
Use of our workspace profiles and API integrations that are possible saves hours of engineering work required for configuration, testing, and development of CIAM-related APIs in case of building the solution with use of a general purpose CIAM platform, API security provider, or authorization server.
Our CIAM SaaS offering is specifically designed for other SaaS applications, so you don’t need to deploy or manage any additional infrastructure. You can spin up a tenant in just a few minutes and try it out for yourself.