IAM Modernization
Minimize risk and cost while quickly and securely delivering business value.

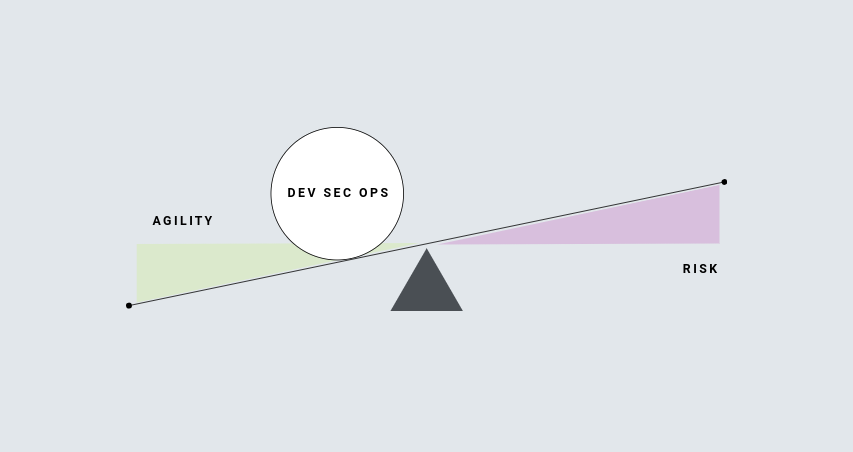
The Delicate Balance of
Agility vs Risk
Successful SaaS platforms deliver value to their customers quickly and safely; this requires a perpetual balance of continuous improvement and risk mitigation. A business that prioritizes one against the other are either leaving money or time on the table… and worse yet, could be exposing itself or its customers to serious security vulnerabilities.
Experts agree that the key to agility is continuous integration and continuous delivery (CI/CD) and the key to mitigating risk is to eliminate implicit trust (i.e. ZERO TRUST), so the desired state must be to build Zero Trust into your CI/CD strategy.
Shift Left: Authorization
The key to mitigating risk in a CI/CD infrastructure is to establish and
AUTOMATE AUTHORIZATION patterns that can be consumed by developers as part of the definition and deployment of their service workloads, thus shifting authorization to the left.
Cloudentity is perfectly positioned to provide the authorization framework for a modern multi-tenant SaaS platform due to its native support for multi-tenancy and its DevOps friendly API-first design.
AUTOMATE AUTHORIZATION patterns that can be consumed by developers as part of the definition and deployment of their service workloads, thus shifting authorization to the left.
Cloudentity is perfectly positioned to provide the authorization framework for a modern multi-tenant SaaS platform due to its native support for multi-tenancy and its DevOps friendly API-first design.
Built-in Multi-Tenancy Support:
Logically separate and delegate the authorization configuration and policies for your customer tenants
Kubernetes & Service Mesh integration:
Enable API/Workload discovery, Policy Enforcement and Transactional Audit
Agent/Machine Authentication and Authorization:
Properly identify non-human users to enforce specific policies for agent-based API calls and service invocations
Policy-as-Code:
Enable policy governance and change management within your SDLC
API First architecture:
Easily integrate application and service authorization configuration into your existing CI/CD pipelines
Scale & Performance:
Grow your business with confidence that Cloudentity can easily scale to meet your needs
CUSTOMER CASE
A leading Application Performance Monitoring provider is building its next-generation platform using Cloudentity software to provide the security foundation for their multi-tenant SaaS platform leveraging a large-scale microservice architecture. By integrating Cloudentity into their core architecture and their CI/CD pipelines, this customer has been able to accelerate their time to market while simultaneously saving hundreds of thousands of dollars in development costs and drastically reducing risk for the business and its customers.
How Cloudentity Can Accelerate Your DevOps
Step 1: Define Baseline Patterns and Policies
By defining a baseline set of application integration patterns and security policies for each customer tenant, the creation of new Cloudentity tenants can be bootstrapped and prepared for use via your existing automation and orchestration platform.
As new and updated policies and configurations become available, they are pushed out to all tenants via deployment pipelines that detect configuration and policy-as-code changes in source control.

Step 2: Automate Policy Adoption
Developers are responsible for policy adoption when they define their applications and APIs.
Policies are selected and attached via the deployment pipeline when the application is initially deployed or subsequently changed.

Step 3: Automate Policy Enforcement
When policies or policy attachments change and they are updated via pipeline invocations of the Authorization Control Plane’s APIs, these changes are automatically propagated to all instances of the MicroPerimeter distributed policy determination point (PDP) using Cloudentity’s internal automation and orchestration.
Updated policies are enforced instantly and consistently across the entire system.

Step 4: Centralize Control & Visibility
Each MicroPerimeter PDP actively discovers new APIs and workloads as they become available and can attach default policy in the case that the API or workload has not adopted a policy during deployment.
Each MicroPerimeter PDP audits the details of every authorization decision and asynchronously reports this audit data to the Authorization Control Plane so that Audit data can be monitored, queried, and used to generate reports from a single, central location.


