Last week, the public was notified about a pretty serious Experian API-related incident leading to the potential public exposure of credit scores for millions of Americans.
What Went Wrong?
Experian’s credit score API drew the attention of a security researcher Bill Demirkapi. It started innocently with him looking around for student loan options. He bumped into direct API access at Experian’s partner website. He was struck by how basic, publicly available personally identifiable information (PII) could be used to access a credit score anonymously. It motivated him to dig deeper and he discovered a vulnerability impacting tens of millions of Experian users.
It turned out that the credit score API that Experian exposes for partners does not require any authentication. Moreover, he discovered any name, surname and address is all one needs to provide to obtain anyone’s highly confidential credit score along with personal risk factors. The API only required date of birth, but didn’t bother to validate it because filling it in with zeros allowed the transaction to pass through.
Experian reacted quickly after being informed about the matter, but the issue was addressed in a way that struck Bill as odd. He expected Experian to solve it globally, not just with a single partner. He deliberately did not provide the partner’s name while raising the issue to motivate Experian to fix it across the board. However, according to Bill Experian identified the partner and worked with them individually to block the unwanted API access. Bill argues that Experian should do more than a simple, quick fix to address such a major vulnerability. Without addressing the root of the problem, this API and other similar ones may be used by other Experian partners in the same manner, causing the same security vulnerability.
What is the Impact of this Breach?Experian states that this incident has been effectively addressed. Nevertheless, it remains unclear for how long this API may have been exposing data in such way. It is also unclear how many individuals’ credit scores have been revealed to unauthorized parties. There are minimal U.S. regulations that protect consumer data like GDPR or CCPA that mandate organizations that store personal information to publicly announce a detailed report of any such breach. Therefore, many of the millions of individuals that were affected by the breach may never become aware that their information was compromised.
This quick reaction from Experian does not help consumers and partners build trust in the institutions that are custodians of our personal data.. Although the incident was addressed, it screams for a more systemic approach to ensure we won't hear of another such API exposing our data tomorrow.
Lastly, the fact that such a critical API intended for partners was accessible without authentication raises doubt about whether proper governance and controls are in place across the board.
How Organizations can Avoid API Vulnerability IssuesModern organizations have quickly learned that APIs are essential for their businesses’ growth. Over time, API proliferation has become challenging for many. Especially when it comes to security and more importantly, access control and governance. In the end, it’s not only about number of APIs, but effective control of numerous integrations between organizations that are necessary to build great user experience for next-generation services.
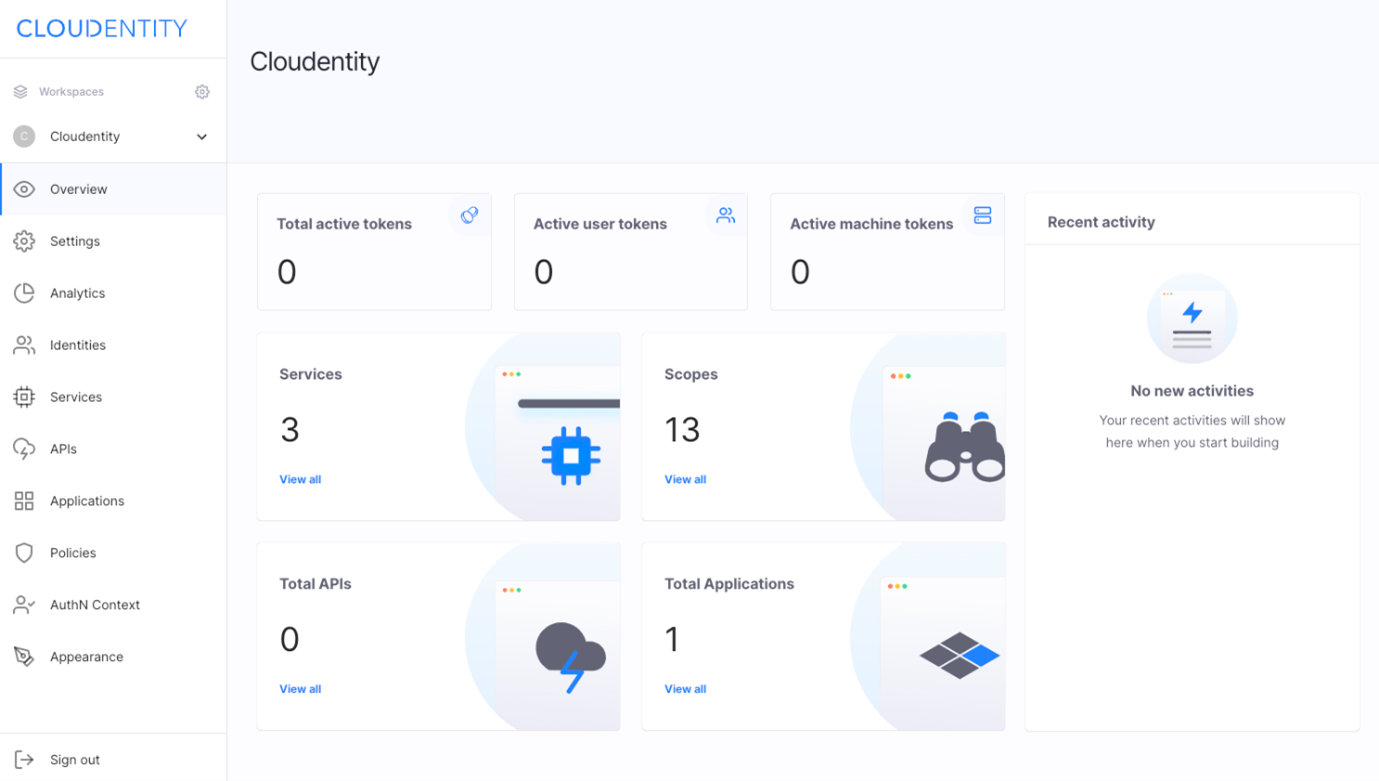
In these environments, security techniques and tools rapidly become obsolete. That is why it’s essential to keep up with the pace with the right technology and solutions for secure dynamic authorization to manage users’ access to important personal data.
Organizations need to know what APIs they expose. It’s not only developers who need to know that, but security teams and DevOps practitioners. The latter two need to understand what each API does and what data it exposes to apply proper access policies. Development pipeline needs to interlace with devsecops pipeline, so that proper policies are applied to every software version. It substantially reduces (or even eliminates) chance of exposure APIs intended for partners and exposing personal information publicly without requiring authentication.
In order to make it possible at current APIs scale and releases pace, organizations need to be equipped with proper tools. Security teams need to understand what API does at macro level need to at least know what data elements are exchanged over such APIs. The tool shall support them in discovery process and allow them to manually or automatically tag APIs. Ideally, the tool would provide them with the option of associating access policies with tags and data elements, so that PII is not accidentally exposed by an API such as Experian’s that does not require authentication.
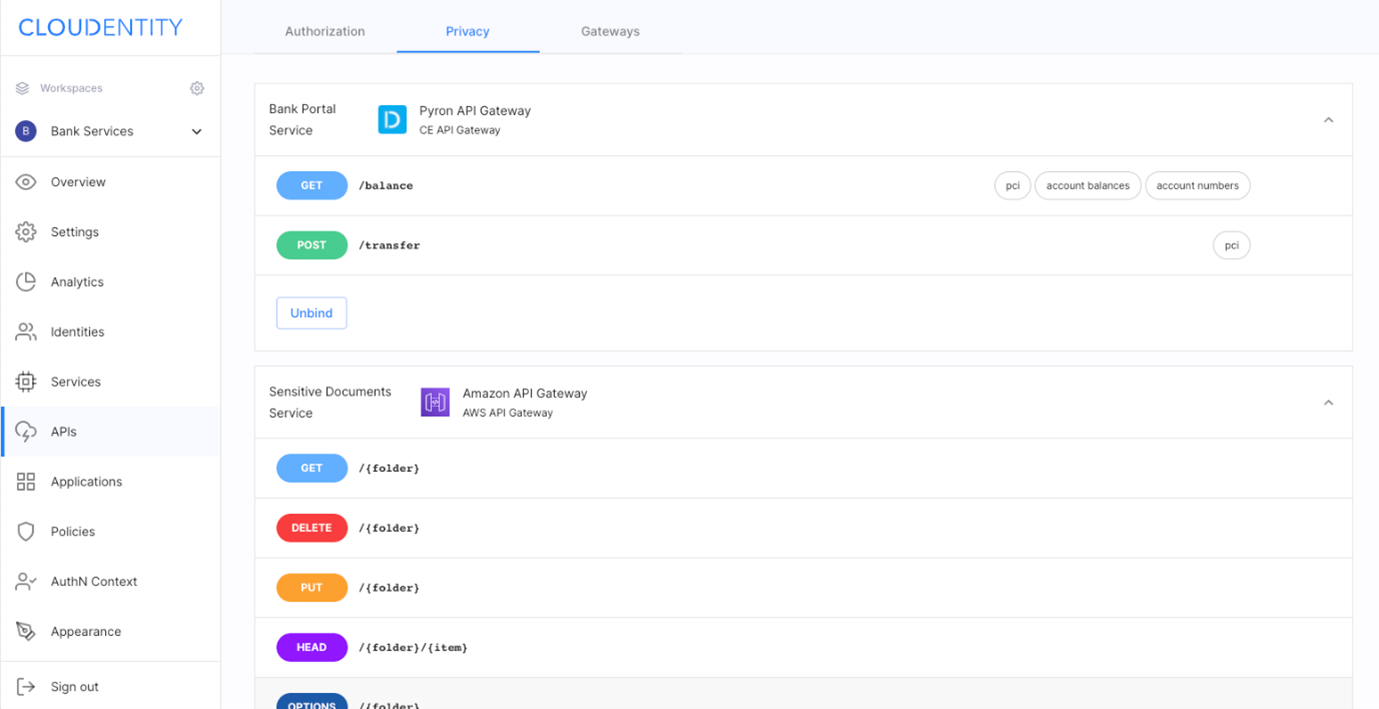
Numerous APIs pose security challenge for organizations itself, however this challenge gets new dimensions when numerous consumers come into picture. Partners, individuals, other third parties. API authorization becomes the key to effectively manage it. There is a couple relevant aspects authorization platform shall provide: - It shall fit into current infrastructure; in particular integrate with existing API gateway and API management to augment often simplistic authorization capabilities of these products not adequate to current needs,
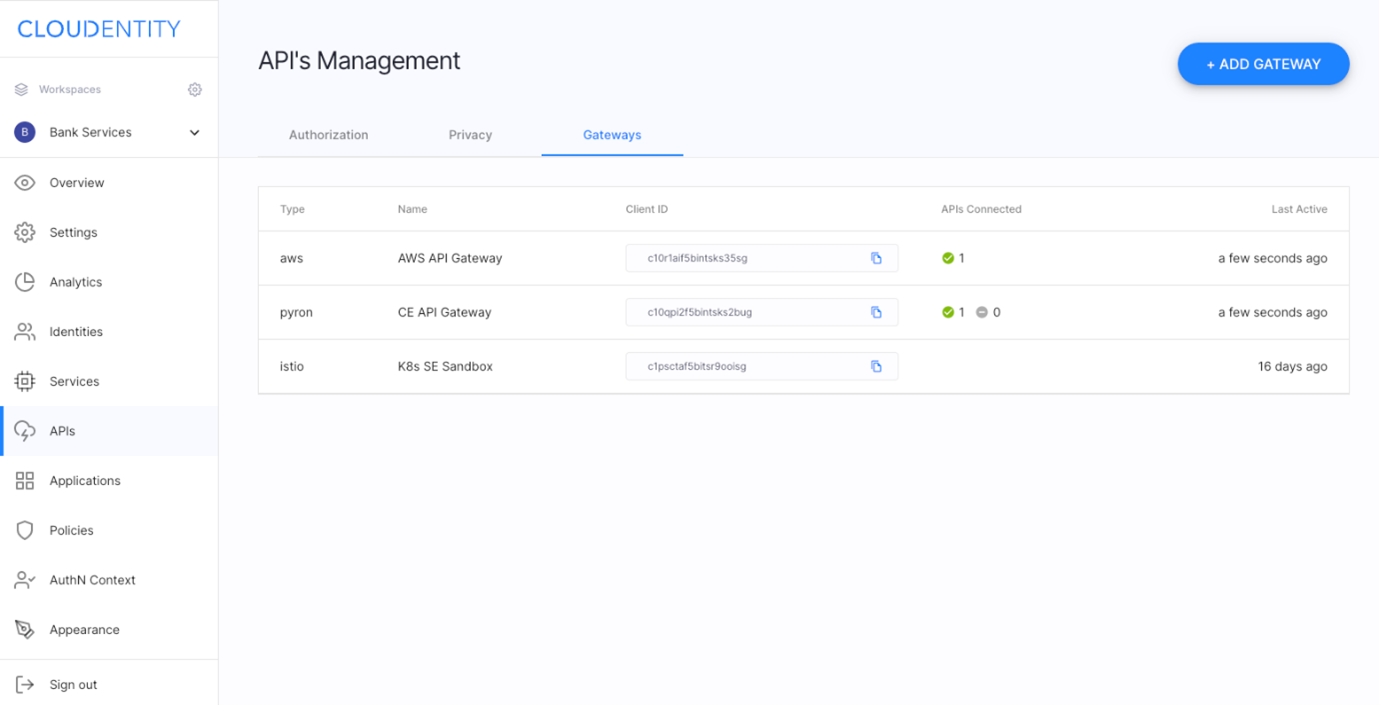
- Recognize APIs as first-class citizens and provide them unique strong identities, allow API authorization policy assignment and make governance and audit at scale easy,
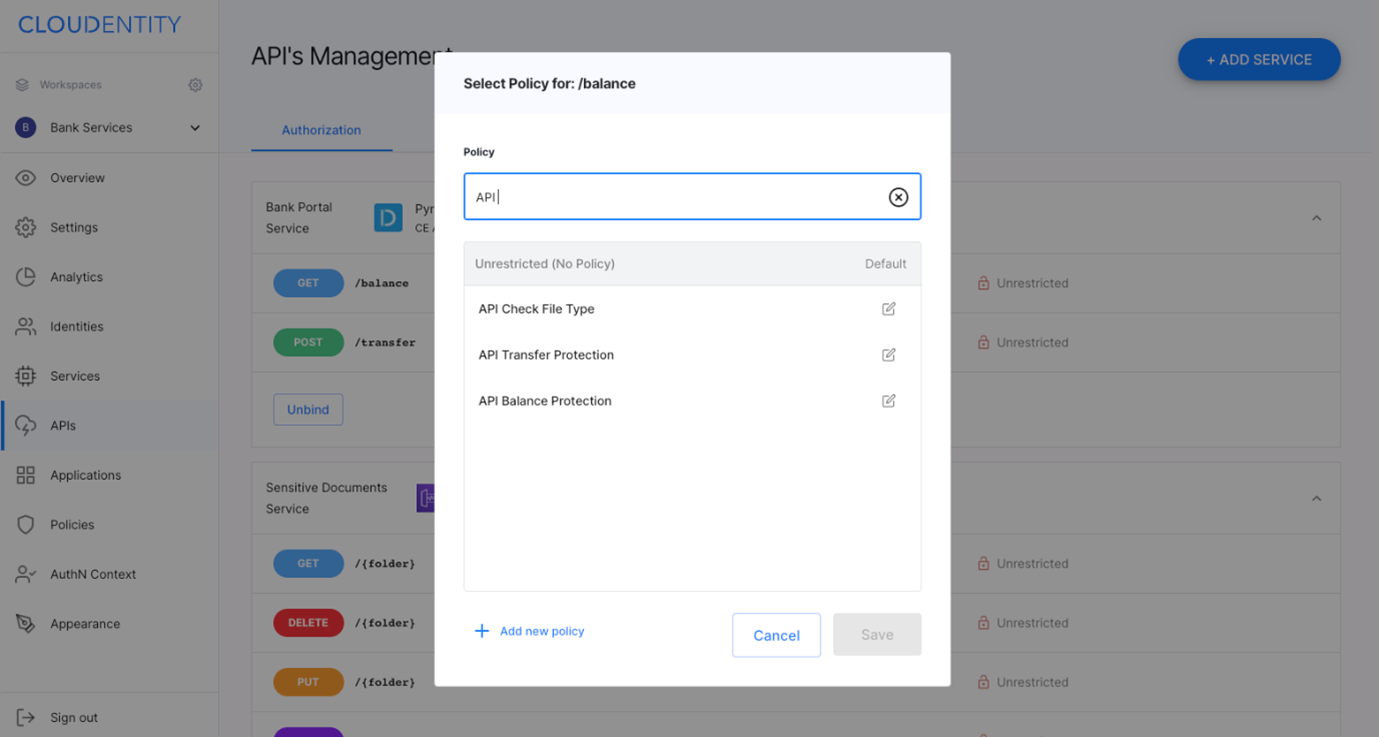
- Include authorization server(s) and allow management of effective API authorization policies that are these days most often spread between authorization server and endpoints, - Integrate with security infrastructure in place and include it in authorization policies
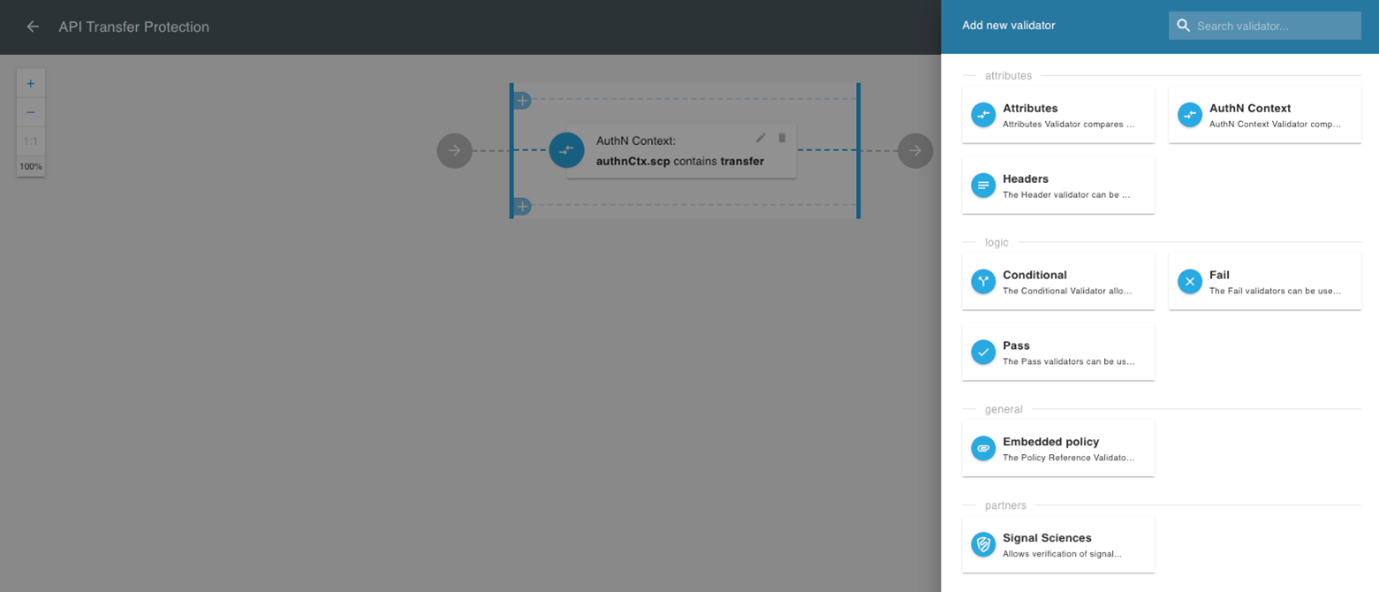
- Support open and regional standards OpenID Connect, FDX, Financial-grade APIs, Rego, SPIFFE - Provide API governance capabilities at scale for North/South and East/West traffic - Machine intelligence; hint about incidents early, detect anomalies and react – notify or automatically apply proper authorization policy


