Versatile Platform for Contemporary Challenges
Employ Cloudentity for Identity, Authorization, and Open Finance Usecases.

Certifiably Dedicated to Open Standards
Check out all certifications and supported open standards.

Extensibility
For organizations with unique workflows, Cloudentity offers customizable extension hooks throughout the platform and webhooks to seamlessly integrate with external services and meet your specific needs.
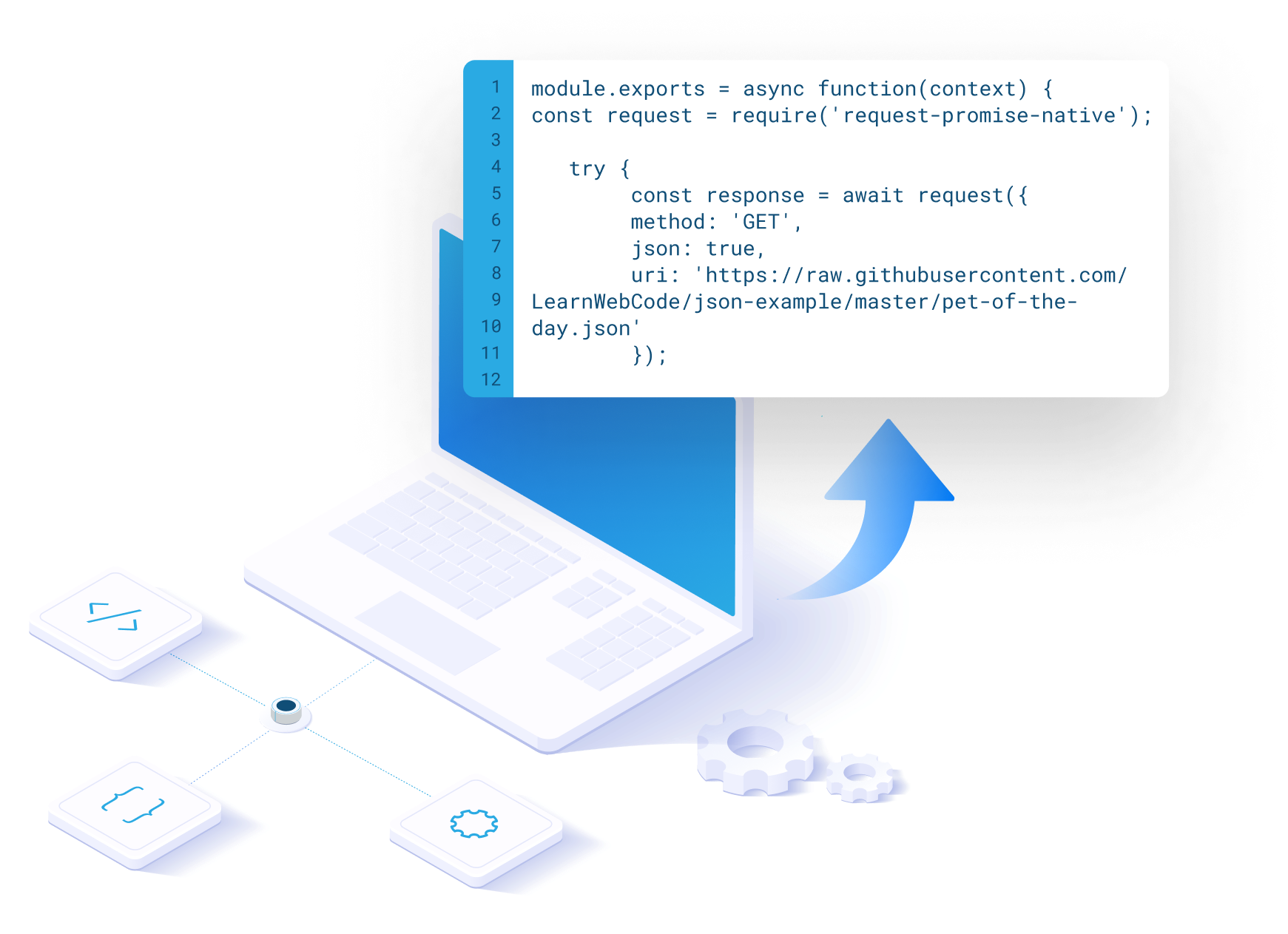
Extension Scripts
Execute JavaScript extension scripts within a secure, isolated environment. Compose, test, and refine scripts using an intuitive IDE-style editor.
Retrieve data from or send data to external systems, enrich token claims, enhance users' attributes, modify the login flow for users, and more.
Notifications
Integrate third-party apps with Cloudentity events, like Open Banking consents or data access requests.
Notify external systems by sending webhooks to designated URLs.
SaaS or Own Deployment - Your Pick
Flexible deployment models for every business needs.
Cloudentity as a Service - SaaS
Seamlessly operated and managed software solution accessible online.
We take care of the ifrastracture, security enhancements, scaling, and continuous updates, ensuring you reap the benefits without the operational hassle.
Public SaaS
SaaS solution accessible online to multiple customers/organizations.
Private SaaS
Cloudentity offers an exclusive SaaS experience tailored for individual customers.

Self-Managed Cloudentity
Deploy, host, maintain, operate, and scale our software within your very own data center or cloud infrastructure.
Customer-Deployed
While you maintain control over your setup and operations, we ensure access to the latest updates.
Hybrid SaaS
Merge the benefits of our SaaS and Customer Deployed models. Choose any mix of Public SaaS, Private SaaS, and Customer Deployed, balancing our hosting convenience with your deployment freedom.
Scalability
Built to scale, our platform caters to companies at any stage, providing steadfast support from startup inception to enterprise success.
Be it tens of users or hundreds of millions, our solution efficiently scales with you.
Be prepared for any eventuality with our platform's effective handling of high-traffic spikes, ensuring uninterrupted operations.




