Why Securing Applications Feels So Difficult
With OAuth, OpenID Connect, Financial Grade API,
and many other specifications getting more broadly
applied accross the web, authorization servers become a crucial component of application and data
security. Authorization platforms have elevated the API data security but most of them fall short
of making the developer’s life easier. Developers are pushing services directly to production more
frequently than ever and are often tasked with responsibilities for paying extra attention to
sharing, governance, authorization, and visibility of data.
With numerous applications consuming APIs, developers must not only apply sufficient authorization controls over requested data in a flexible manner (especially with very fast evolving data sharing specifications), but also be able to visualize and manage all those applications holistically. Additionally, each application can serve a different purpose, exposes different APIs and services, has its own credentials that can or cannot be shared with other parties. Apps can be also developed by a different team, by a third party, and more. With this complex permutation and combination of possibilities, it is quite easy to make mistakes and leak data unknowingly if we do not keep track of how, when, and by whom the APIs are consumed. Sounds like a lot of work, doesn’t it? Securing these applications and gaining the appropriate transparency and effective access control is not trivial with traditional authorization platforms and raw authorization servers anymore.
At Cloudentity, we are developers too and we also need to secure our APIs. This is why we added the Topology View to our platform! To make yours lives easier (and ours, too, to be honest).
Visualize Application Authorization With Cloudentity Topology View
Cloudentity Topology View enables developers to add an authorization layer to applications easier than ever before and get much better transparency when securing applications. Wait, what? What topology has to do with applications? you may ask. At Cloudentity, we define apps as a service and a client application. Topology, sometimes called rubber-sheet geometry, studies properties of spaces invariant under any continuous deformation. Similar to rubber, the objects can be streched and contracted, but cannot be broken. Just like our authorization layer. You have probably already connected the dots. We added apps (services and client apps) to the authorization space and that’s how the Application Topology View was introduced to our platform. Sounds good, right?
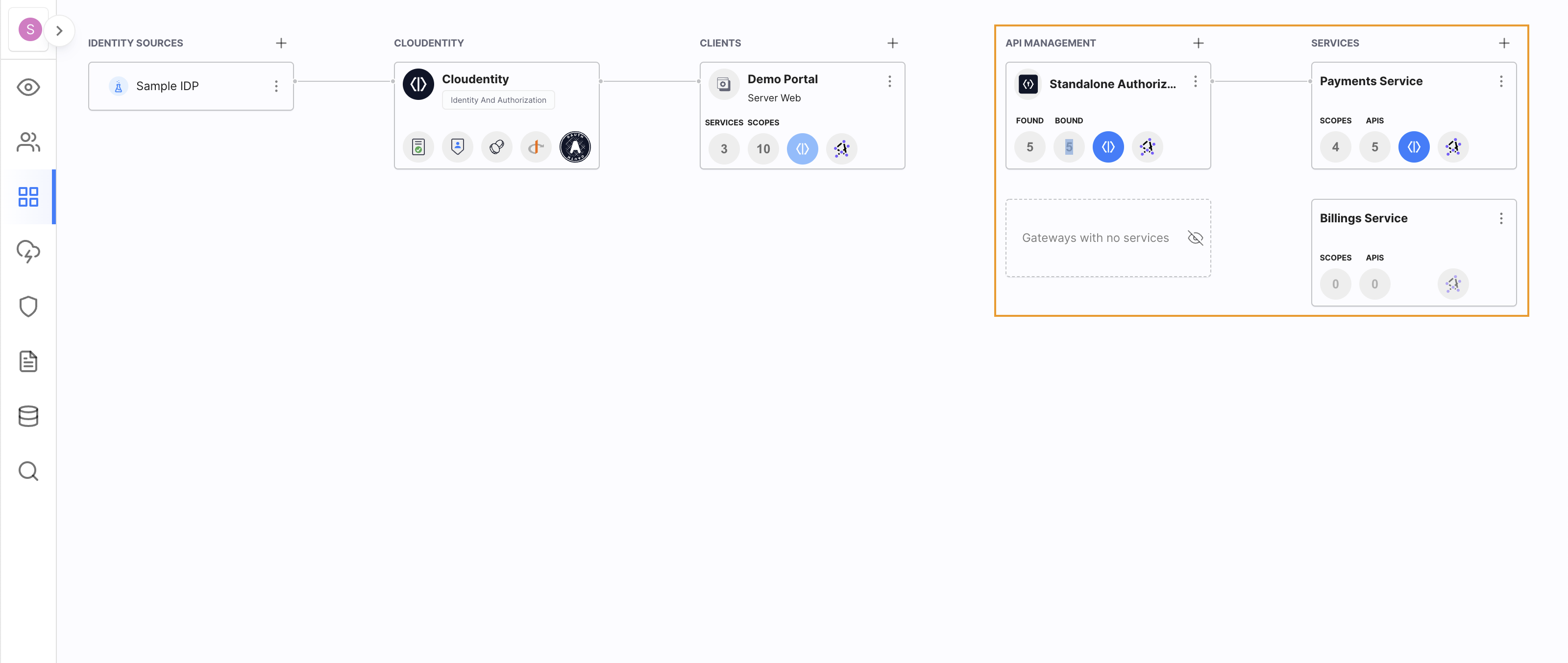
Cloudentity Application Topology View does indeed make your life easier. Within one view, you can:
-
Create services, import APIs, and define scopes to protect access to services.
-
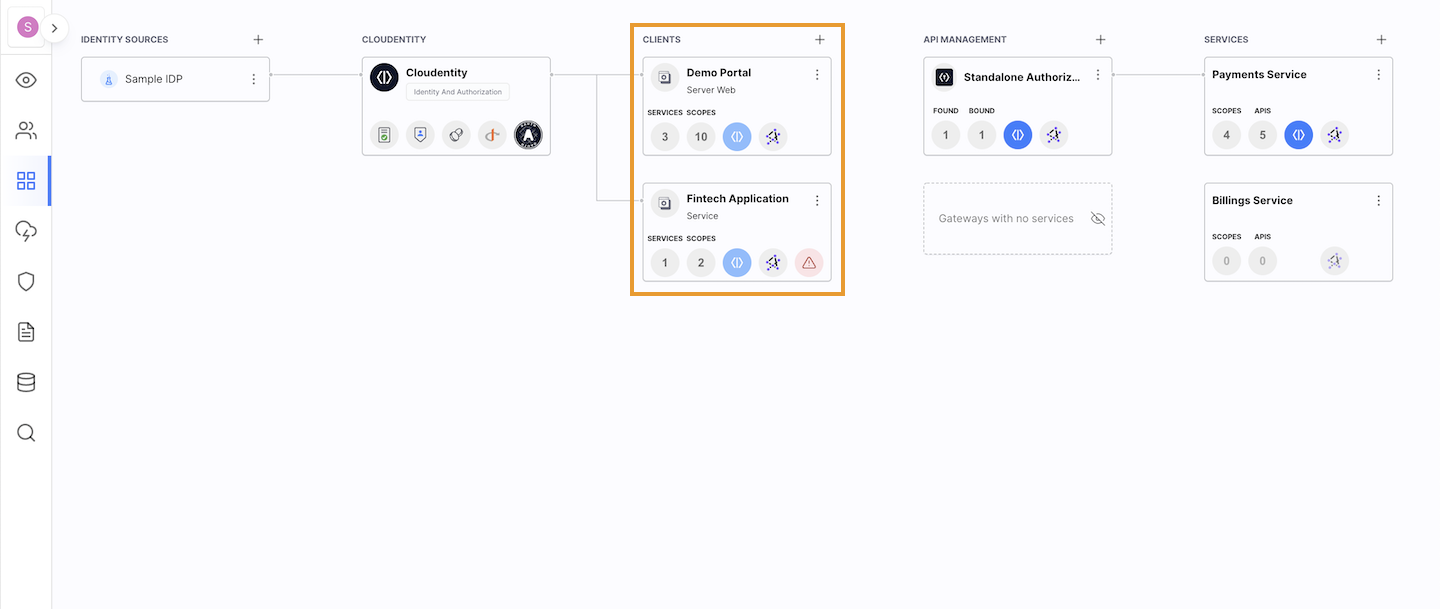
Define client applications that consume the services you created.
-
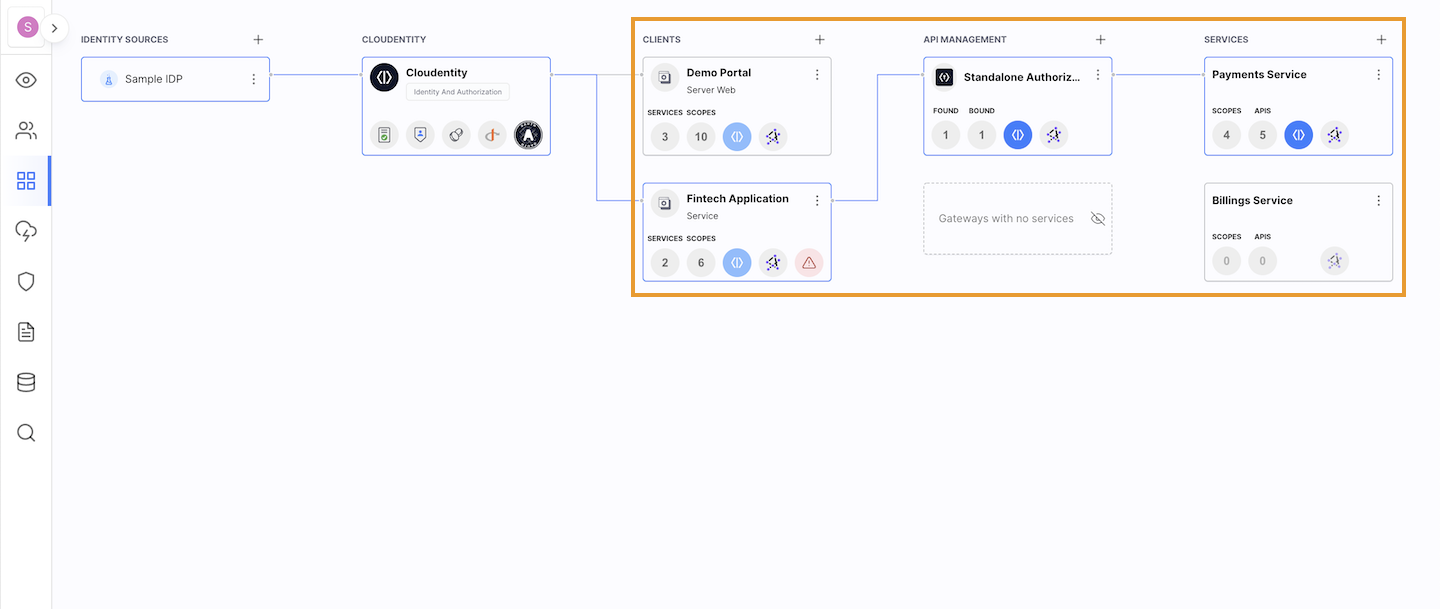
Subscribe applications to service scopes.
Before After 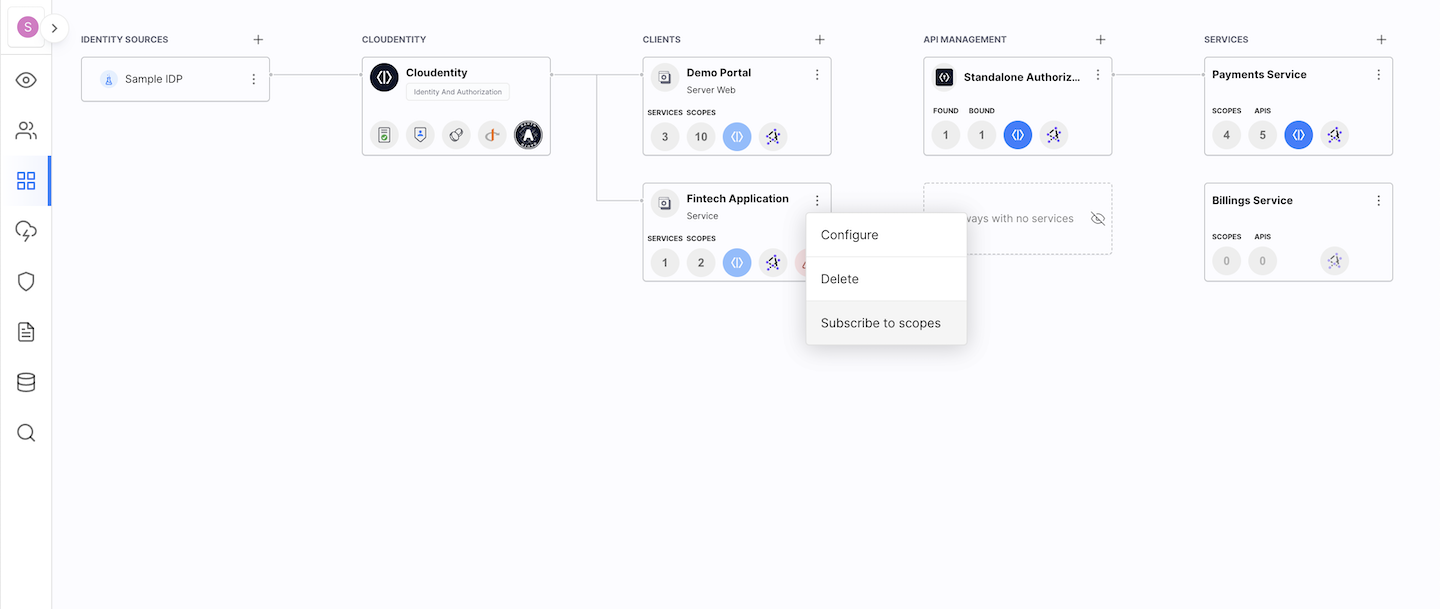
-
Define identity sources you wish the user to use when accessing an application.
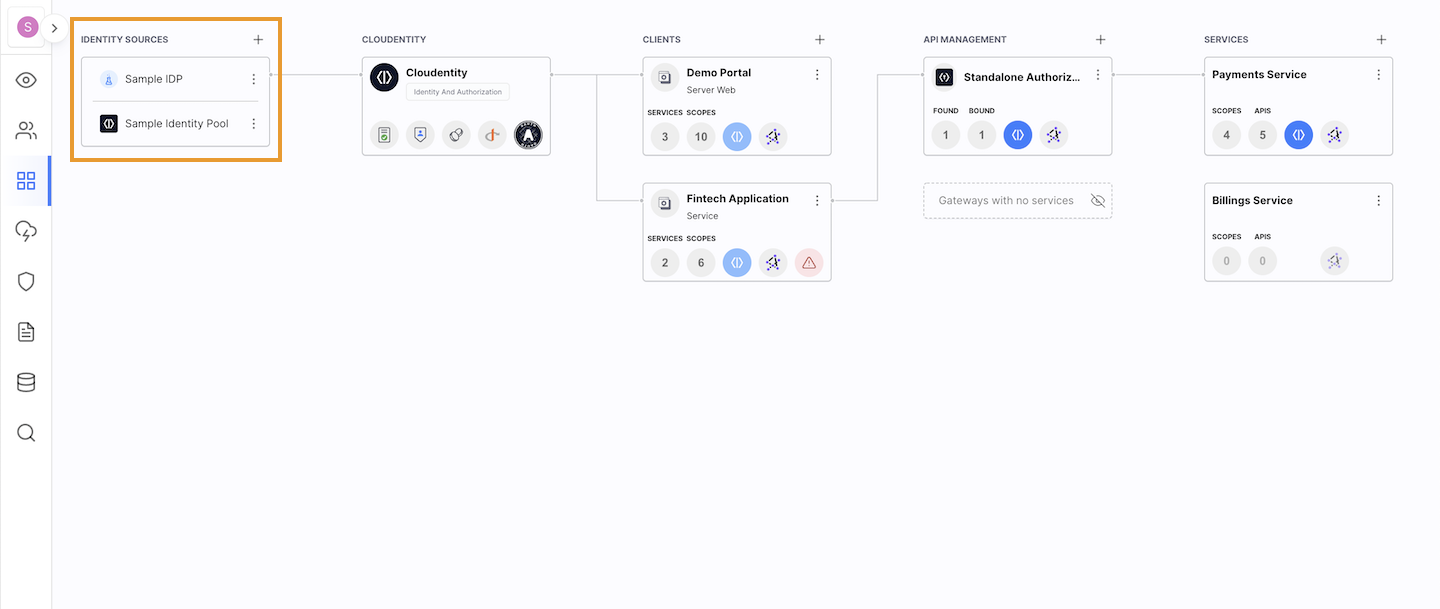
Once you have the application topology set up, you can control access - and, of course, you can do it within the Topology View. Visualize connections between different components of your perimeter. You can enable token exchange to exchange third party tokens to security tokens issued by the Cloudentity platform. See OAuth and profile scopes configured for your workspace, and more.
Cloudentity Topology View gives you a possibility to achieve more in one place without jumping through different tabs. Powerful WYSIWYG editors let you control and visualize the entire perimeter of your secured system. Why wait? Check it out yourself.
Register for free to get access to a Cloudentity tenant and start exploring our platform!
