SSO and Identity Providers
Cloudentity can act as identity provider and integrates seamlessly with external identity and authentication providers using open standards such as OIDC, SAML, and SCIM or custom connectors. This way we enable your platform requests to be authorized on top of authentication from users authenticated from any source including a direct customer(B2C), business partner customer(B2B2C) etc or any customer/user model you want to use.
BYOID as Extended SSO
Cloudentity Bring Your Own IDP approach allows organizations to seamlessly in self-service fashion configure their identity providers for user authentication. It also opens up organizations to configure their applications to be accessed by partner identities. This is enabler for digital expansion at scale beyond single source of authenticated users and is considered a fundamental cornerstone in the modernization and expansion journey.
BYOID Concept
Bring your Own Identity Provider (BYOID) concept allows you to take advantage of Cloudentity modern authorization capabilities without replacing your existing Identity and Access Management (IAM) product(s).
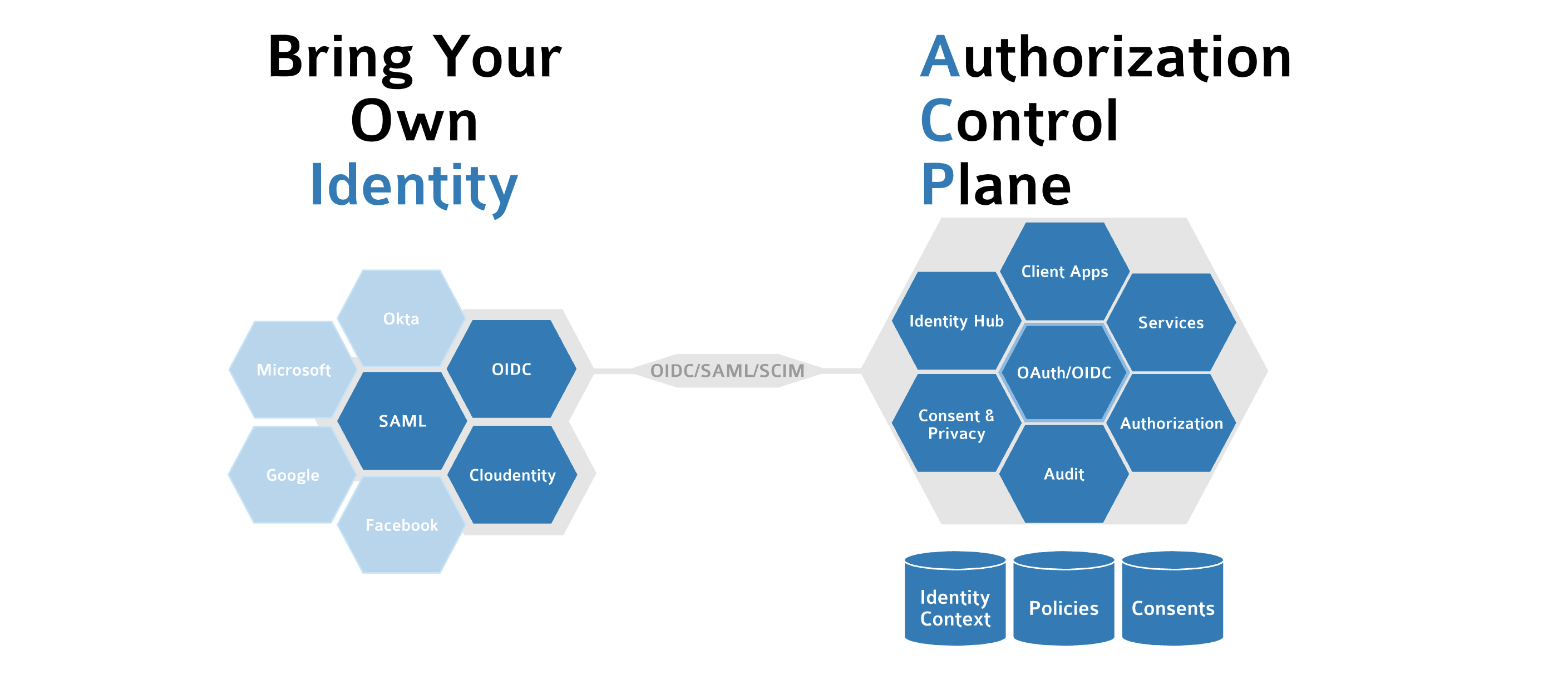
Multiple Identity provider integrations can be configured at the workspace/organization level opening a flexible way to integrate with multitude of identity providers within the organization or to allow partner level identity providers. The workspace-level integration enables the organization to utilize a distinct source of the user data for administrators, service owners, developers (including the third-party ones), and consumers, ensuring a distinct separation of the duties enforcement.
During the user authentication with external identity providers, regardless of the protocol, Cloudentity creates an ephemeral authentication context for the authenticated user which can also be enhanced with other data enrichment points. This meta session includes all data attributes provided by the external provider.
Dynamic User Session Enrichement
Cloudentity can extend the authentication context and enrich additional custom attributes from different sources. Such combined attributes are stored in the Cloudentity’s authentication context in a normalized fashion and can be utilized as part of the identity context attribute validation, scope governance and other dynamic authorization policy rules in various authorization token minting, governance and enforcement workflows within Cloudentity