Authentication Overview
Cloudentity by default provides user authentication and SSO for connected applications and their APIs. Add an application lets leverage user authentication.
SaaS Applications User Authentication Requirements
Nearly every SaaS application requires user authentication. Naturally SaaS applications require multi-tenant user authentication services ideally delivered by a SaaS identity platform. The latter is especially the case for SaaS Applications for Business.
Early stage SaaS businesses value the speed of setting up the user authentication and management, scale on demand and pay-per-use approach.
As SaaS applications mature and use cases become more complex, the authorization and access control becomes more important and ideally must be provided by identity platform.
Authentication for Consumer and Business SaaS Apps
Consumer and Business SaaS apps are the two most prominent use cases with different user authentication requirements:
-
Consumer SaaS Apps: passwordless login, social providers, simplicity
-
SaaS Applications for Business: SSO with delegated administration, enterprise identity providers, SAML.
Cloudentity as SaaS Identity and Authorization platform covers both use cases. It is especially usefult to address the latter given the advanced authorization engine and unique multi-tenancy capabilities.
Cloudentity as Identity Provider and SSO/Bring Your Own Identity
Cloudentity by itself has capabilities to store users across various user populations and authenticate them. Read more about Cloudentity authentication capabilities below.
Nearly every SaaS app requires to authenticate with external identity providers. Cloudentity provides a way for businesses accounts to connect their own identity providers in self-service fashion.
Authentication Methods
Cloudentity Identity Pools can be connected to workspaces without any hassle in order to enable your users to authenticate themselves before acessing your applications.
Passwordless Authentication with Passkeys
When a user is asked to sign-in to an app or website, the user approves the sign-in with the same biometric or PIN that the user has to unlock the device (phone, computer or security key). The app or website can use this mechanism instead of the traditional (and insecure) username and password.
As with most authentication mechanisms, passkey login begins with a registration phase. Cloudentity passkey implementation conforms to the WebAuthn specification.
The Web Authentication API (WebAuthn) is an open standard for passwordless web-based authentication introduced by the World Wide Web Consortium (W3C), Fast Identity Online (FIDO) and other industry leaders. The specification can be viewed here.
The WebAuthn protocol uses asymmetric (public-key) cryptography in conjunction with ownership and biometric-based authentication mechanisms (passkeys) to provide a more robust login framework than knowledge-based schemes like passwords.
In accordance with FIDO standards, passkeys serve as a superior alternative to traditional passwords, offering quicker, simpler, and safer logins to websites and applications across a user’s various devices. Unlike conventional passwords, passkeys maintain a high level of security at all times and are resilient against phishing attacks.
Enable passwordless authentication
User Authentication with Verification Codes
Cloudentity sends a unique, time-limited verification code to the user’s pre-registered email address or mobile phone via SMS. Such verification code can be also generated and provided to the custom sign-in application to enable it to provide codes to users over channels.
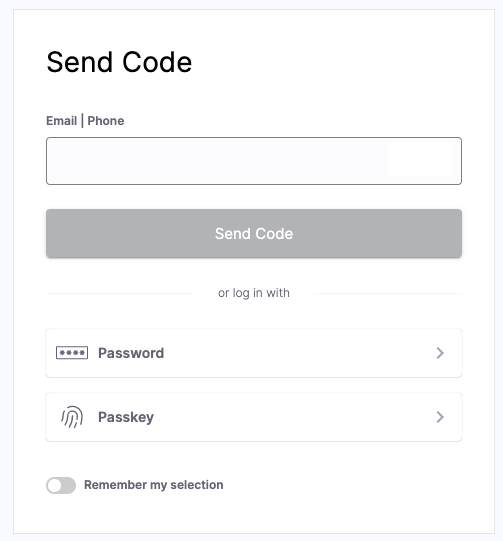
With verification codes, users do not use a password - they use the code along their email or phone number to authenticate themselves. It makes verification codes more secure than using passwords, since codes are time-limited and sent to the user for one time use.
Enable authentication with verification codes
User Authentication with Magic Links
After the user provides their email, Cloudentity generates a unique, time-limited link and sends it to the user’s email address or mobile number. When the user selects the provided link, they are automatically redirected to the application and signed in.
At present, Cloudentity does not support the use of Magic Links via a user interface. The feature can only be utilized through API integration and custom sign-in pages.
User Authentication with Identifier and Password
User provides a unique identifier (such as a username, email, or phone number) and a password. Cloudentity verifies this information against stored user data. If the provided credentials match the stored ones, the user is granted access. This method is a common and fundamental way of securing user accounts.
External Authentication Providers
| What You Can Connect | What Users See |
|---|---|
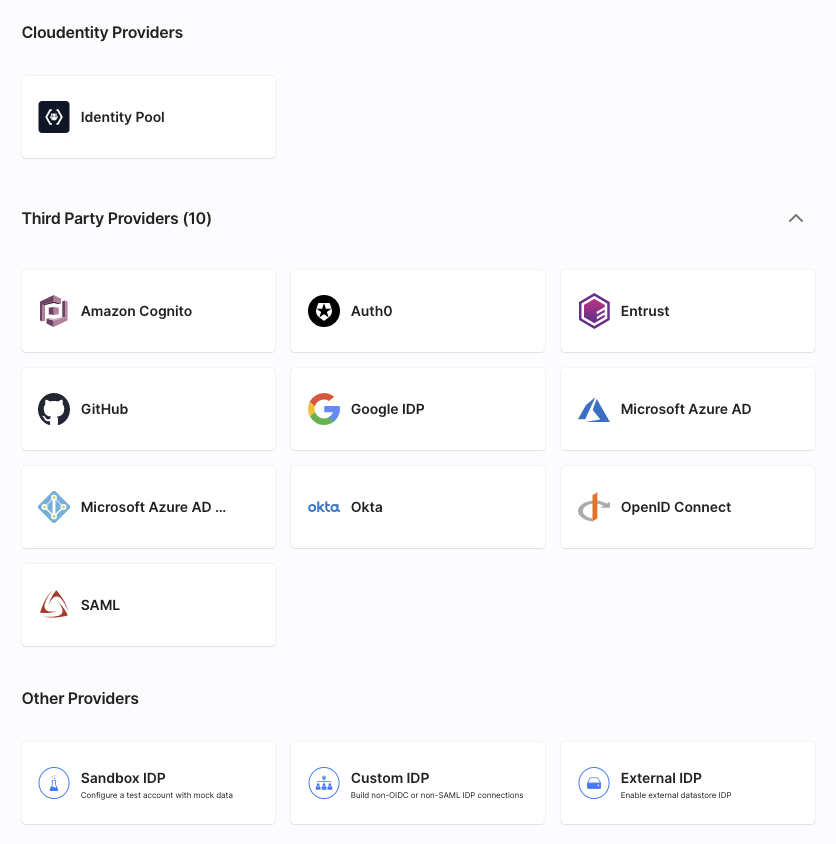 |
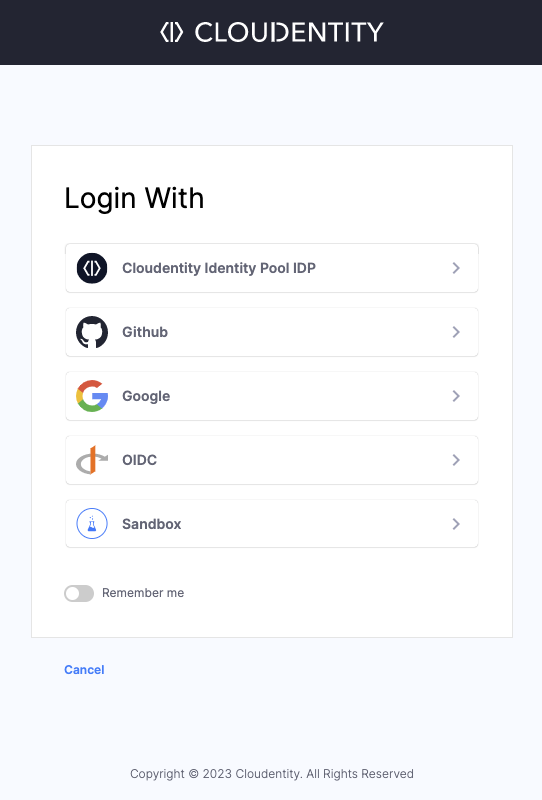 |
Social Login
Users use their existing login information from a social networking service, such as Facebook, Google, or GitHub, to sign into a third-party application. It simplifies the process by allowing users to authenticate themselves without the need to create and remember a new username and password for each site.
You can connect Google or GitHub to allow users to sign in using their social networking service.
Single Sign-On / Enterprise Authentication Providers
Business scenarios very often require identity federation where identities are created and managed within across multiple domains or enterprises. Cloudentity allows you to:
-
Integrate with SAML apps
-
Standardize user data coming from different IDPs into one common authentication context schema
Approach to Authentication
Developers that are responsible for providing application users with a possibility to sign in to their accounts must decide between employing a universal or embedded login flow.
With Universal Login, users attempting to log in are redirected to a central domain where authentication takes place, before being redirected back to the app. Conversely, an embedded login flow keeps users within the same page, avoiding redirection to a central domain. The login widget is presented on the same page, and users' credentials are sent to the authentication provider for verification. In a web app, this process involves a cross-origin request.
At Cloudentity, we firmly believe that centralized (universal) authentication is the most robust and secure solution in the majority of cases! It eliminates cross-origin request present in the embedded authentication. By harnessing the full potential of OAuth, it not only satisfies the most stringent security requirements but also delivers a highly adaptable authentication experience.