October 31, 2022
v2.8.0 Highlights
Comply with Brazilian Open Insurance Initiative
Cloudentity platform now fully supports the Brazilian Open Insurance (OPIN) initiative.
-
The Open Finance Brazil type of workspace is configured to provide industry-specific OPIN configuration, for example, OPIN scopes.
-
Added permission mappings and groups validation required by OPIN. It can be used in the consent creation endpoint.
-
Added the following endpoints from the OPIN spec for consent creation and management:
-
Added DCR requirements support coming from the Open Insurance specification. This includes:
-
Requirement of using mTLS for DCR registration
-
Software statement parsing and validation for the model provided by the specification
-
Software role to scope mapping during DCR
-
-
Extended mTLS aliases in the OAuth wellknown endpoint to include the backchannel authentication endpoint when Client Initiated Backchannel Authentication method is enabled as required by the OPIN specification.
-
Add an option to configure supported
acr(Authentication Context Class Reference) values in the authorization server’s OAuth advanced settings. Workspaces now use whatever is configured in the settings instead of an internal hardcoded list.
Utilize Improved Identity Pools
We added a bunch of new improvements to Cloudentity Identity Pools:
-
User credentials now include the
expiresAtparameter. Once the password expires, it fails verification, and the user needs to either reset it or change.Password expiry can be utilized when migrating users from external identity sources without their passwords defined. Just provide no password and set the expiry date for a date in the past to trigger password change for your users.
-
Added option to set Preferred Authentication Mechanism useful when both password and OTPs are enabled for an IDP. Now, it is possible to pick the default one that shows up on the login screen.
-
Cloudentity Platform admin users can now manage user identifiers and addresses within Cloudentity Identity Pools. Admins can add new identifiers with the email, mobile, UUID types, or even identifiers coming from external sources. Additionally, admins can add new verifiable email or mobile addresses for users and define whether the address is verified or not.
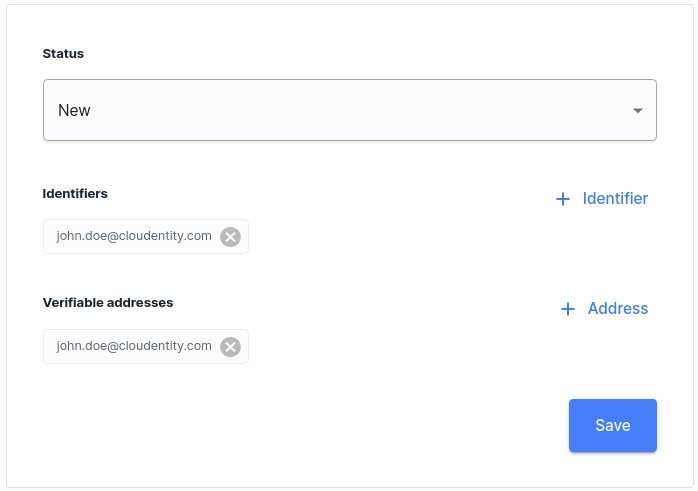
-
Refactored Identity APIs to enable developers to extend them more easily.
Cache Requests in Cloudentity Authorizers
In this release, we improved the Cloudentity authorizer’s integration with the Open Policy Agent’s REGO language so that the caching features in the REGO http.send() function are effective. You can now use the following fields in your REGO policies:
-
cache- Cache HTTP response across OPA queries. Default: false. -
force_cache- Cache HTTP response across OPA queries and override cache directives defined by the server. Default: false. -
force_cache_duration_seconds- If theforce_cachefield is set totrue, this field specifies the duration in seconds for the freshness of a cached response.
In Cloudentity v2.8.0, the authorizers provide an inter-query cache that persists
across policy
validations, which enables calls to the http.send() method to access cached responses from
previous policy validations. The cache is recreated on each API discovery cycle, so the duration of
cached responses is limited by the authorizer’s discovery interval.
discovery:
enabled: true # when true, API discovery is enabled
interval: 30s # how often discovery is performed
The cache size can be configured via the rego_inter_query_cache_size configuration setting for
Cloudentity authorizers:
enforcement:
rego_inter_query_cache_size: 1000000 # maximum size for the Rego inter-query builtin cache
Major Additions and Changes
[ AUT-7438 ] REGO policies that authorize access to APIs via the MicroPerimeter Authorizers can now take advantage of the Open Policy Agent (OPA) inter-query cache.
[ AUT-6982 ] The redirect_uri query parameter is added for custom login and consent pages.
As a result, when a login session is timed out, the user is redirected to the client application,
instead of the 404 page.
[ AUT-7166 ] Audit logs now include the report on clients' incorrect certificates when
registering the clients via the
/dcr endpoint
within the CDR workplace.
It grounds on the new DCR Create and Reject audit events available for use in webhooks.
{
"tenant_id": "default",
"server_id": "default",
"event_id": "c7e4bd0ecd7948838e77ca1c4118e872",
"timestamp": "2022-09-30T12:45:08.321549+02:00",
"context": null,
"event_subject": "dcr",
"action": "created",
"metadata": {
"ip": "127.0.0.1",
"user_agent": "curl/7.81.0",
"trace_id": "208ecf49ef99b78358fb9285c4bc9d68"
},
"payload": {
"dcr_created": {
"x_real_ip": "",
"x_forwarded_for": "",
"remote_addr": "127.0.0.1:40136",
"user_agent": "curl/7.81.0",
"client_details": {
"client_id": "4762daae3b7643db83d0b743c010e11c",
"client_name": "Sample DCR client",
"grant_types": [
"authorization_code"
],
"token_endpoint_auth_method": "client_secret_basic",
"scopes": [
"email",
"offline_access",
"openid",
"profile"
],
"certificate_bound_access_token": false,
"software_statement_provided": false
}
}
}
}
{
"tenant_id": "default",
"server_id": "default",
"event_id": "092be4c6121442d297a919b80a68c976",
"timestamp": "2022-09-30T13:05:43.64787+02:00",
"context": null,
"event_subject": "dcr",
"action": "rejected",
"metadata": {
"ip": "127.0.0.1",
"user_agent": "curl/7.81.0",
"trace_id": "971705ff1d12bdaae945884f83779931"
},
"payload": {
"dcr_rejected": {
"x_real_ip": "",
"x_forwarded_for": "",
"remote_addr": "127.0.0.1:45220",
"user_agent": "curl/7.81.0",
"error": "invalid_request",
"error_cause": "",
"error_description": "client certificate is required when certificate bound registration token is enabled",
"error_hint": "Make sure that the various parameters are correct, be aware of case sensitivity and trim your parameters. Make sure that the client you are using has exactly whitelisted the redirect_uri you specified."
}
}
}
[ AUT-7281 ] Added support for the BASE64_NON_URL_ENCODED_DER client certificate format.
Info
BASE64_NON_URL_ENCODED_DERis the base64-encoded format without URL encoding.
[ AUT-7419 ] Critical and high-level vulnerabilities with Alpine Edge are fixed.
[ AUT-7471 ] For the resource owner credentials grant flow, tokens are issued after applying IDP mapping.
[ AUT-7105 ] Added password expiration support. Once a password is expired, its verification fails and the user is required to change their password.
The expiration date can be set with the following options:
-
Reset password: also available for already expired passwords
-
Change password: can be used for valid passwords
The feature grounds on the expiresAt attribute. It can come in handy for cases when users are migrated
without passwords—set no password with the expiredAt date in the past. As a result, the user is required
to change their password.
Invalid password:
`{"error_description":"request lacks valid authentication credentials for the target
resource","status_code":401}`
Expired password:
`{"error_description":"request lacks valid authentication credentials for the target resource",
"error_hint":"credential expired","status_code":401}`
Breaking Changes
[ AUT-7185 ] Now, token_endpoint_auth_method is validated for all client applications—not only registered
by developers but also created by administrators as well as with
DCR.
The validation is based on the server’s token_endpoint-auth_methods.
[ AUT-7264 ] From this version on, the Azure B2C connector accepts custom domains.
[ AUT-7307 ] The open redirection occurrence on logout is eliminated.
[ AUT-7341 ] POST /fdx/consents/introspect returns FDXConsent.
This covers the following changes:
-
The
getFDXConsentvalue is returned with unified response data instead of theGET /consents/{consentID}response. -
The granted resources and their IDs are returned with the
Resourcesvalue instead ofGrantedResources. -
The number of consent fields returned by the
/introspectendpoint is limited togetFDXConsent.
Please find the /introspect endpoint API reference
updated.
Minor Enhancements
[ AUT-6740 ] Added the filter options for the List FDX Consents endpoint.
Now you can filter the returned list of FDX consents by the following parameters:
-
client_id -
status -
resource: provideresourceTypeand the list ofids
Also, the pagination search is available.
Request body:
{
"after_consent_id": "string",
"before_consent_id": "string",
"client_id": "string",
"limit": 0,
"order": "string",
"resource": {
"ids": [
"string"
],
"resourceType": "ACCOUNT"
},
"sort": "string",
"status": [
"string"
],
"types":
[
"string"
]
}
[ AUT-7080 ] ETags explanation added to the Cloudentity API documentation.
[ AUT-7188 ] Refactored Identity Pools APIs: the admin and system endpoints are split. No changes to the endpoints themselves; however, some changes can arise when rendering libraries from Swagger (for example, package changes).
[ AUT-7248 ] Changed the DCR register error codes from 409 (client already exists) to 400 and 422 (validation error). As a result, 400 now complies with the specification.
[ AUT-7274 ] CDR compliance: consent sharing_duration and ADR client statuses are validated before
login.
[ AUT-7275 ] Added API management for the Revoke FDX Consents endpoint.
With it, you can revoke consents and all the related tokens per client application. For this, pass the client_id
and RevocationDetails parameters.
API returns the number of revoked consents.
The example request body:
{
"RevocationDetails": {
"initiator":
"\"INDIVIDUAL\"",
"reason": "\"USER_ACTION\""
},
"client_id": "string"
}
[ AUT-7299 ] Added the revocation_reason query parameter to the following endpoints:
-
DELETERevoke CDR Arrangements -
DELETERevoke CDR Arrangement
revocation_reason helps keep track of why an arrangement has been revoked.
The CDR arrangement revocation reason field must not exceed 256 characters in length.
[ AUT-7277 ] The redirect_uri parameter is now validated when redirect_uri isn’t explicitly
requested in the /authorize endpoint
call since the client features only one Redirect URI.
[ AUT-7463 ] Added validation for calls to the /identity API
Now, when identity_pool_id
points to a non-existing pool, the call fails fast and with the same response.
Bug Fixes
[ AUT-7125 ] For FAPI Advanced compliance, a request object check has been added to make sure
that the exp claim is no longer than 60 minutes after
the nbf claim, as the FAPI specification requires, see - 5.2.2 -> 13.
[ AUT-7273 ] Added a tooltip indicating that a user has multiple identifiers under Identity Pool > Users > Identifiers. Added a UI entry in the Identity Provider’s user view indicating all identifiers of that user registered in Identity Pool.
[ AUT-7339 ] Removed the unnecessary Subscribe to Scopes link for SAML clients in the application topology view.
[ AUT-7400 ] Addressed a number of vulnerabilities found in Cloudentity’s Docker image.
[ AUT-7464 ] Adjusted the DCR flow for the Open Banking Brazil workspace. Now, when the
/register endpoint is used, the following rules are enforced:
-
If
request_object_signing_algis supplied and the value is not PS256, an error is returned. -
If there is no
request_object_signing_algvalue supplied, an implicit value of PS256 is set.
This validation is enforced for both signed and unsigned DCR registration requests.
[ AUT-7256 ] Fixed a bug where if one user wanted to grant 2 consents, and the scopes of the second consent were granted with the first consent, they were not granted for the second consent at all.
If the list of scopes in the first and second consent was the same, then the second consent was granted with no scopes at all.
Recommended Database Versions
| Database | Version |
|---|---|
| CockroachDB | 22.1.1 |
| Redis | 6.2.7 |
| TimescaleDB | 2.8.0 (with Postgres 14.5) |
