June 30, 2023
Highlights
Easily Connect SAML IDPs
We added a bunch improvements to the process of connecting SAML IDPs:
-
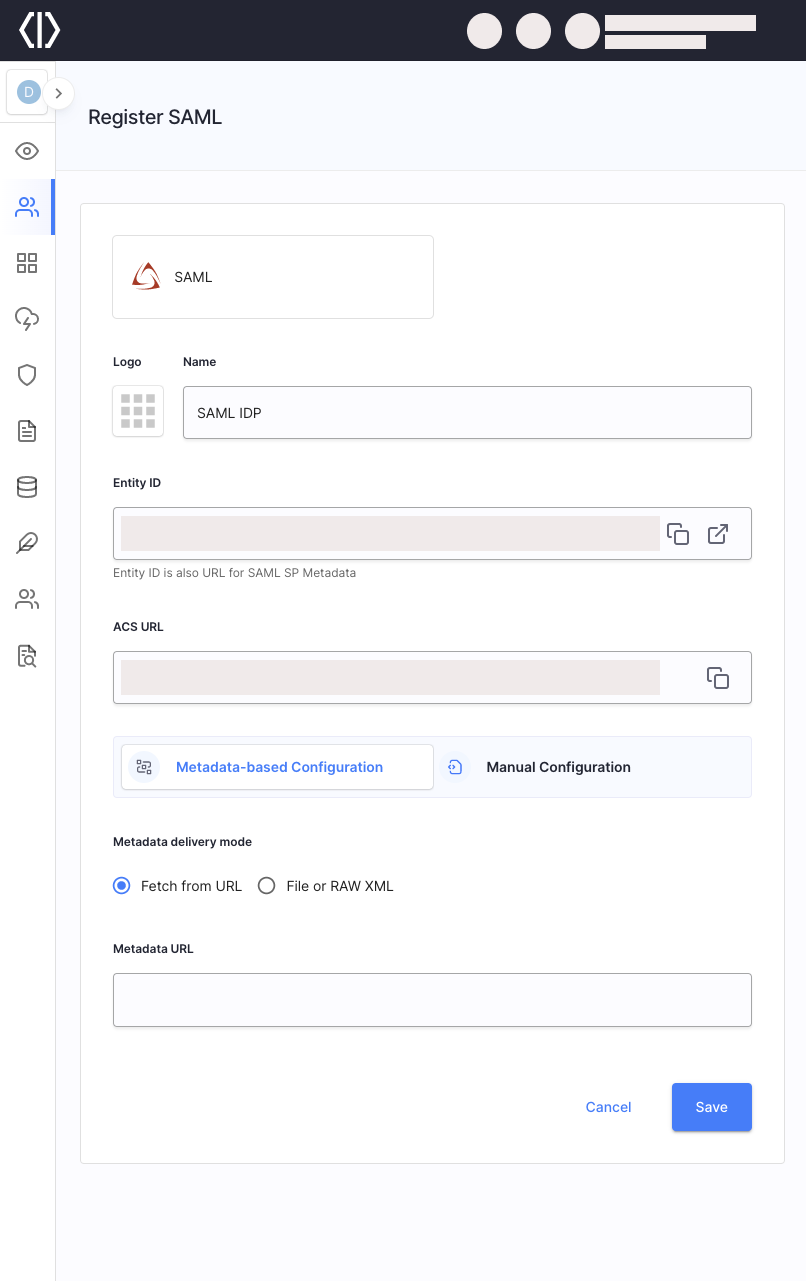
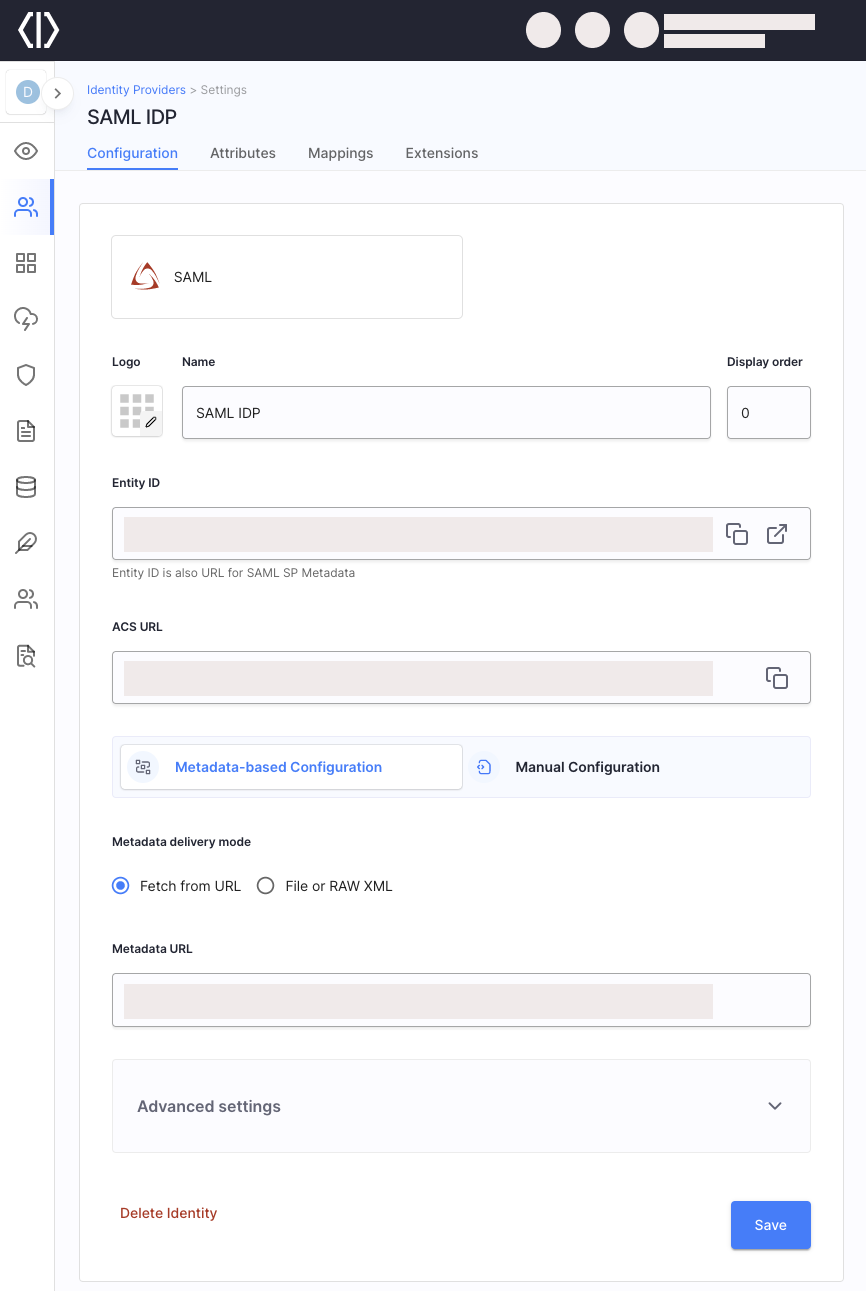
You can switch between two configuration options: Metadata-based Configuration which enables Cloudentity to fetch your IDP configuration from a metadata endpoint, and Manual Configuration which enables you to configure the IDP manually.
-
To enhance the IDP (Identity Provider) configuration process, we have included two new fields to the SAML IDP.
-
The Entity ID field allows you to specify the unique identifier for the IDP entity.
-
The ACS URL field enables you to input the Assertion Consumer Service URL for the IDP. These additions provide more flexibility and customization options when setting up IDPs in our application.
-
| IDP Connection | IDP Configuration |
|---|---|
 |
 |
Configure Custom Token and Code TTLs for Client Apps
You can now configure custom Token and Code Time-to-Live periods for client apps that take precedence over the TTLs you apply at the authorization server level (Settings » Tokens » TTL). Learn how.
Enrich Token Claims for Client Application
It is now possible to assign Token Claim Enrichment Extensions directly to a client application. Extensions attached at the client level affect only the client they are assigned to and are executed after Extensions at the server level (if there are any). Learn how.
Breaking Changes
[ AUT-9213 ] Introduced Appearance section in tenant settings with two items: Branding and Themes.
Branding is Cloudentity basic styling editor with primary and header colours, logo, and font url customization.
Themes is a themes list, where Default theme is represented as regular theme but only for preview ( read-only mode). Both theme name and workspace name in the table navigate to the theme editor or workspace appearance view respectively.
Workspace level Appearance view has a decreased number of previews available depending on the server type. For organizations (if feature enabled) workspace and login page preview is only enabled. For other workspace types, it is possible to preview only the Login Page and Consent Pages.
[ AUT-9218 ] Return Scopes in promote config APIs without IDs.
[ AUT-9197 ] Return claims in promote config APIs without ClaimID.
[ AUT-9393 ] Extension libraries changes:
-
Bumped fission JS dependencies
-
superagentremoved from the fission dependencies because of vulnerability problems.axioscan be used instead. -
Dependencies versions update:
-
aws-sdk2.1306.0 -> 2.1404.0 -
mongodb5.0.0 -> 5.6.0 -
mongoose6.9.0 -> 7.3.1 - major version update -
xml2js0.4.23 -> 0.6.0
-
Major Additions and Changes
[ AUT-9288 ] Policy execution points are now presented in place where policy is applied: servers, scopes,
clients.
Policy execution points whose target is scope use scope names instead of scope id to
identify scope in tree dump structure.
[ AUT-9326 ] Private JWKS is not returned as part of the Server configuration promotion APIs for dynamic client registration and trust anchor.
Minor enhancements
[ AUT-6000 ] Allow providing user/client context to the /policy/validate endpoint even if the
authorizer is used without the access token.
[ AUT-9116 ] Configuration Promotion APIs improvements.
Root level and Tenant level APIs:
-
GET /api/hub/promote/config -
PATCH /api/hub/promote/config-rfc6902 -
PATCH /api/hub/promote/config-rfc7396 -
GET /api/hub/{tid}/promote/config -
PATCH /api/{tid}/hub/promote/config-rfc6902 -
PATCH /api/{tid}/hub/promote/config-rfc7396
now operate on Tenant level (TreeTenant structure)
which means the API exports a whole tenant (without its ID) and patch expects a singular tenant.
Workspace level APIs:
-
GET /api/hub/{tid}/workspaces/{wid}/promote/config -
PATCH /api/hub/{tid}/workspaces/{wid}/promote/config-rfc6902 -
PATCH /api/hub/{tid}/workspaces/{wid}/promote/config-rfc7396
now operate on Workspace level (TreeServer structure) which means the APIs export a workspace
(without its ID) and patch expects a singular workspace.
Derived clients are moved to the workspace level APIs. It means that each workspace
has its derived_clients field where there are all clients form system workspace that are
referenced by this workspace.
For Root level and Tenant level APIs for now there is empty
derived_clients for each server because derived clients can be accessed directly in system
workspace part of the dump.
For now only Rfc7396 patch is able to handle derived_clients.
Remember
Configuration Promotion APIs are still in the alpha phase. If you wish to use them, contact Cloudentity Support Team. The APIs may be still a subject to breaking changes and not fully functional.
[ AUT-9135 ] Possible to configure appearance/styling per workspace.
Tenant and workspace/organization stylings are now applied to admin/b2b portals.
If workspace/organization don’t have custom styling set, tenant styling is used.
[ AUT-9145 ] Instead of having client_ids for clients that lives in System workspace and have
references in current workspace (i.e. for gateway) new config migration API’s embeds client
configuration. Also RFC7396-compliant API allows to modify/create such embedded clients.
[ AUT-9150 ] If identity pool is connected to more than one IDP from two different workspaces Cloudentity prompts the administrator to choose which workspace styling apply to sent message.
It applies to the following messages:
- send/resend activation message
- reset password
- verify address
- challenge otp
When the administrator selects Remember theme selection for this pool settings will be stored in pool metadata under “theme_workspace_id” value and can be modified in Settings tab.
[ AUT-9166 ] It’s now possible to Self register, Activate and Reset Password without the outh2 context.
[ AUT-9184 ] Add general purpose metadata field to the user identifier model.
[ AUT-9198 ] Add new federated identifier type used for JIT provisioning
[ AUT-9217 ] Root and System level config promotion APIs now support Pools and Schemas.
[ AUT-9226 ] The administrator can now update client configuration and set custom token and code TTLs (access_token_ttl, id_token_ttl, refresh_token_ttl, authorization_code_ttl) that override workspace-level TTLs.
[ AUT-9246 ] Add a possibility for clients to have a Token Claim Enrichment script assigned. The script is executed after server token pre-minting script. Learn more on how to assign Extensions to clients.
[ AUT-9325 ] Escape commas in TLS certificate attribute values when parsing subjectDN. Add support for JURISDICTIONST attribute in TLS certificate.
[ AUT-9379 ] Added new management endpoint for retrieving Open Finance Brasil consents by ID.
To use this endpoint, a client must authorize with the system workspace and obtain a token with
the manage_openbanking_consents scope.
[ AUT-9384 ] Add identifiers with details (value, type) to list users API.
[ AUT-9390 ] Added user_id to the inspect extended OTP endpoint response. It allows customers to fetch user information when processing this code.
Bug fixes
[ AUT-9084 ] Override tenant ID in new patch API to disallow cross-tenant operations
[ AUT-9099 ] After logging into Google IDP as User A, the logged-in session from Google’s perspective is cached. So after entering User B’s identifier in Cloudentity login screen, with instant-redirect, User A’s cached Google session results in User A’s session on the Cloudentity side.
The solution in this PR is to provide
the entered identifier as a login_hint to Google (and other OIDC providers). This prompts the IDP
to autofill the identifier at login instead of trusting its cached session.
Two new IDP attributes are added:
-
version: Controls automatic behavior of new IDPs before (version = 1) and after (version = 2) this change. -
send_login_hint: Whether to send thelogin_hintparameter. Only exists for OIDC-enabled IDPs.
If an IDP exists before this change, send_login_hint is
disabled by default. If an IDP is created after this change, send_login_hint is enabled by
default. In either case, this can be overridden in the Admin UI for OIDC-based IDPs.
[ AUT-9134 ] Deleted custom app disappears from list after deletion.
[ AUT-9214 ] Sender friendly name should is for Cloudentity as an option.
[ AUT-9255 ] Remove Verify OTP Challenge action from user Manage menu
[ AUT-9291 ] Identifier case-insensitive not checked on create pool init fix.
[ AUT-9347 ] Request to identity pool idp without SSO enabled should fail with interaction_required
[ AUT-9388 ] Fixing bug where null-valued logout_redirect_domains crashed SSO configuration view.
This change
fixes a bug where if the logout_redirect_domains of an oauth server’s SSO configuration had a
null value, the SSO configuration screen couldn’t load.
Now an empty or null
logout_redirect_domains will be omitted from the oauth server response object.
[ AUT-9401 ] AUT-9401 Empty passwordless settings
[ AUT-9398 ] No warning when NO Authentication Mechanism in the pool
Recommended Database Versions
| Database | Version |
|---|---|
| CockroachDB | 22.2.8 |
| Redis | 6.2.12 |
| TimescaleDB | 2.10.3 (with Postgres 14.5) |