Prerequisites
Add Outgoing SAML Assertion Attributes
-
Select OAuth » Tokens & Claims » Claims » SAML Assertion Attributes » + ADD CLAIM.
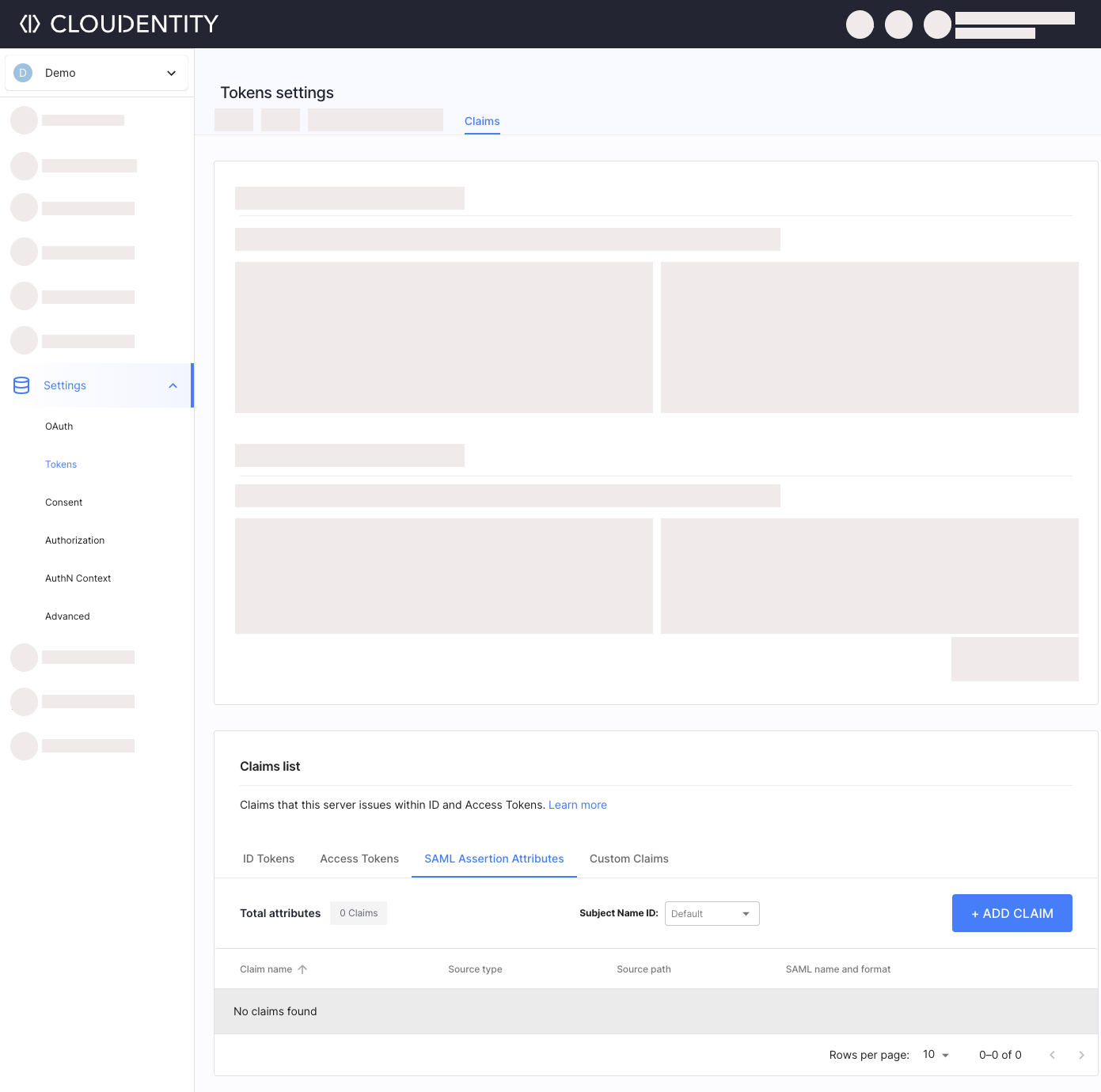
-
Fill in the Add claim form with and select Add.
Parameter Description Claim name Claim name in Cloudentity. Source type How the source value for the claim is retrieved. Authentication context is a set of attributes mapped from data sent by IDP acting on behalf of the user. Client means an application registered in Cloudentity. Workspace provides metadata about the workspace. Source path Specific attribute available in the source. Output source path Exact attribute name representing this claim in the token. SAML Name SAML attribute name issued with your Service Provider’s assertion, for example urn:oid:2.5.4.10.SAML Attribute Format SAML attribute format, for example urn:oasis:names:tc:SAML:2.0:attrname-format:uri.
The attribute will be included in the SAML Assertion sent to service providers
Consider the following example:
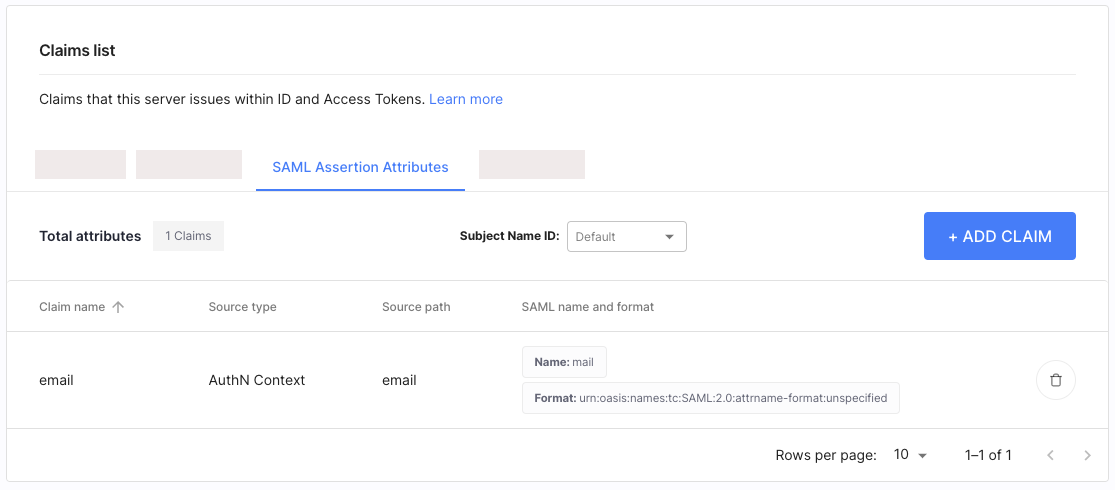
If we add an email attribute with source type set to AuthN Context, source path set to
email, SAML name set to mail and with the SAML format set to
urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified,
the outgoing SAML Assertion sent to the Service Provider has the following attribute included:
<saml2:AttributeStatement>
<saml2:Attribute Name="mail" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<saml2:AttributeValue
xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">johndoe@example.com
</saml2:AttributeValue>
</saml2:Attribute>
</saml2:AttributeStatement>
Next Steps
If your SAML IDP enables users to sign into OAuth-based client applications, be sure to define Token Claims as well.