About Cloudentity Authorizers
Cloudentity provides the possibility to integrate API Gateways and Service Meshes into its authorization platform in order to secure them with policies. To that end, it uses authorizers - system components responsible for discovering APIs and Services and synchronizing policies with those APIs and Services.
An effective authorization policy that controls resource access is usually distributed between an authorization server and a resource server. In a distributed application system, resource servers are composed of microservices that expose certain APIs for external consumption. Cloudentity provides comprehensive and easy way to govern authorization for APIs and service meshes.
Cloudentity needs to know about all APIs to assign authorization policies to each one of them, and to provide visibility and governance. Cloudentity’s authorizers discover APIs by periodically querying the API Gateway. Cloudentity regularly refreshes its API schema, in order to stay in sync with the gateway’s configuration. By doing so, Cloudentity provides a tool for DevSecOps engineers that lets them effectively manage and govern authorization that spans across hybrid and multi-cloud systems.
Cloudentity provides authorization for APIs, maintaining a unified developer experience in heterogeneous systems.
Below, you can find a list of key benefits that come with integrating ACP and your API Gateway or Service Mesh:
- Dynamic externalized authorization for the service mesh,
- Microservice level API discovery,
- Unified authorization for microservices in the mesh and beyond,
- Authorization server integration.
- Distributed authorization with centralized management,
- ABAC, RBAC, Fine-grained authorization,
- Authorization policy governance,
- API authorization unification across diversified environments,
- WYSIWYG policy editor with ready to use building blocks, policy versioning, REGO based policies,
- Policy decisioning context (for example, user, security feed, request, threat analytics),
- Policy callouts to external APIs.
Policies and gateway integrations are managed centrally at the authorization server level.
OAuth Token Exchange
Cloudentity’s authorizers are capable of exchanging incoming third-party access tokens to internal access tokens and use them as the means of authenticating your request to access protected data. See Using third-party access tokens for access control for details.
GraphQL API Protection
GraphQL is a query language for APIs and a runtime for fulfilling those queries with your existing data. Cloudentity can protect GraphQL services deployed behind Istio - see Protecting GraphQL APIs for details.
GitOps
Cloudentity, when integrated with an API Gateway or Service Mesh, brings GitOps approach microservice mesh authorization making it an ideal tool for DevSecOpses. Authorization policies are stored in Git repositories, and when a policy is changed, Cloudentity pulls the changes from the Git repository. This practice makes policies easy to version and use in DevSecOps pipelines. At the same time, policies are easy to audit and design using a visual editor.
Declarative configuration import further enables the GitOps approach. You can store the configuration inside your Git repository and have your configuration and infrastructure as code. In this case, your Git repository acts as a single source of truth for your Cloudentity configuration. This leads to increased productivity for your teams, enhanced developer experience, improved stability, reliability, and consistency.
It is possible to configure your Cloudentity deployment declaratively using the acp-cd Helm Chart. The configuration import can be used for all Cloudentity deployment types including the Cloudentity SaaS deployment or Cloudentity deployment on Kubernetes.
The acp-cd Helm Chart is responsible for creating a Kubernetes job that seeds Cloudentity with configuration. You can, for example, define client applications, gateways (both for multi-tenant and single-tenant authorizers), policies, and APIs.
For details, read Declarative configuration import.
Apigee X/Apigee Edge
Apigee X and Apigee Edge are API development and management platforms. Both provide an abstract layer for your backend service APIs and provide security, rate limiting, quotas, analytics, and more. The gateways are based on the concepts of API products and API Proxies. An API proxy is a facade on Apigee Gateway that is, in fact, a set of configuration files and policies for one or more APIs. API proxies are usually delivered to consumers in groups. Such groups are called API products. To control an API proxy, flows that contain logic, condition statements, error handling, and more, are added to the proxy. Such flows can be used to introduce an external API access control enforcement tool and this is where Cloudentity steps in.
Authorization is vast enough to be addressed by specialized products and its requirements are driven by non-trivial and real-life use cases and security requirements. Since Apigee Gateways allow to externalize authorization decisioning using their flows features, you can bring in Cloudentity to satisfy the authorization requirements and to greatly improve your API security.
With Cloudentity you can centrally manage authorization policies at the authorization server level. Cloudentity discovers APIs by pulling them from your Apigee Edge or Apigee X platform and, later on, allows you to apply authorization policies to enforce access control and to prevent your APIs from unauthorized access. When Cloudentity is integrated with Apigee X or Edge platform, it implements externalized policy decision at the endpoint level enforced by the proxies provided by Apigee Gateways. Beyond this service-to-service authorization use case, it also covers authorization and authentication use cases related to the consumption of externally exposed APIs.
Apigee X/Edge Authorizer is a built-in Cloudentity feature that allows you to download a package with the authorizer to easily integrate your Cloudentity instance with your Apigee X/Edge platform. It provides you with a possibility to automatically install a shared flow that contains two policies provided out-of-the-box that are responsible for communicating with the Apigee X/Edge Authorizer, blocking/allowing the request depending on its decision, and for delivering an error status as a response to an unauthorized call to your protected APIs.
For detailed information on how to use both Apigee authorizers, see:
Istio Authorizer
Istio service mesh is designed to address the challenges that come with the transition of monolythic applications towards a distributed microservice architecture by providing the right infrastructure.
Istio as a service mesh implementation offloads developers from solving repeatable problems within microservices themselves. It also provides DevOps engineers and administrators with tools they need to effectively operate, manage, and secure distributed applications at scale.
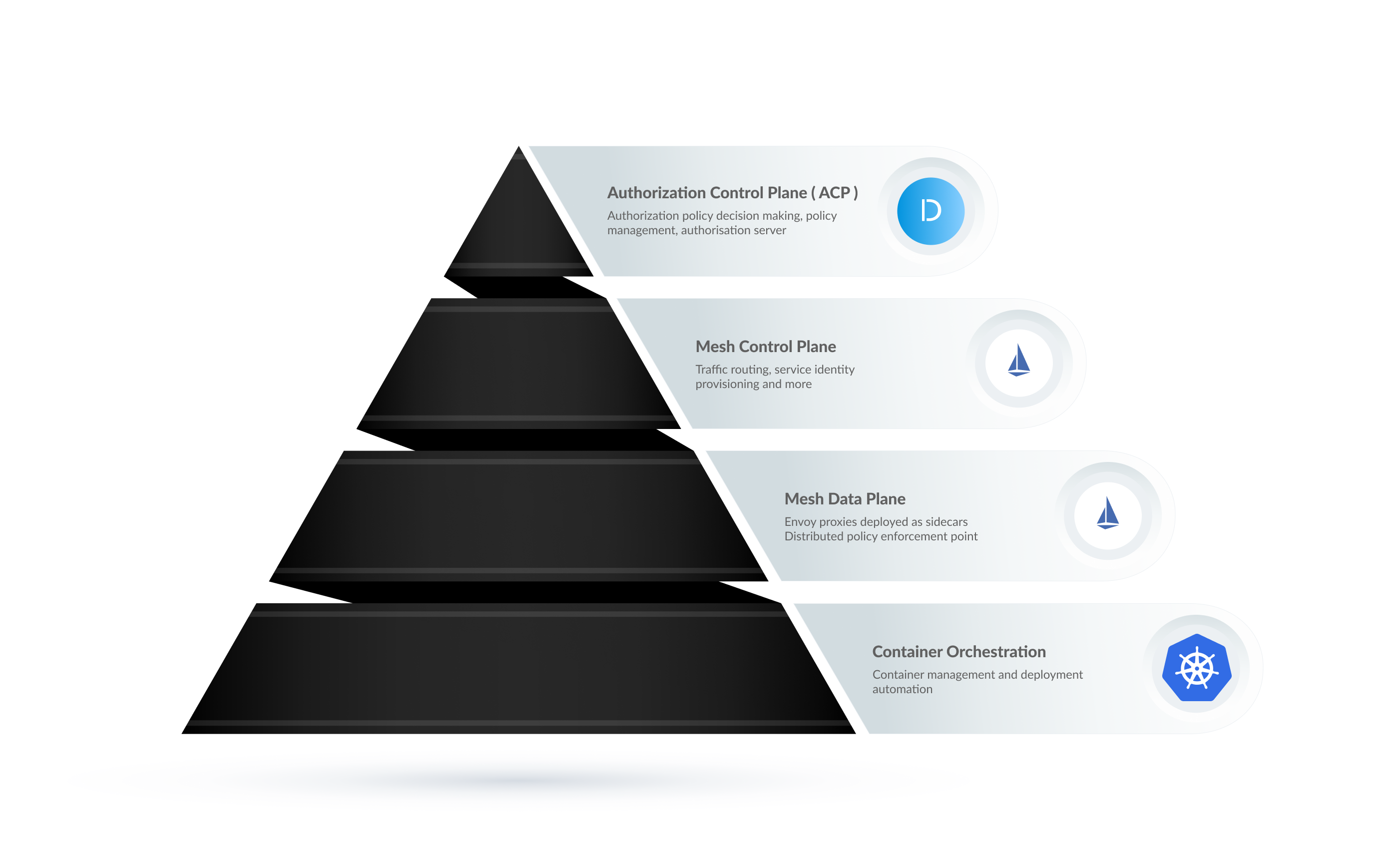
For detailed information on how to integrate Istio with Cloudentity, see Dynamic Authorization and API Discovery for Istio.
Kong Authorizer
Kong or Kong API Gateway is a cloud-native, platform-agnostic, scalable API Gateway distinguished for its high performance and extensibility via plugins.
By providing proxying, routing, load balancing, health checking, authentication, and more, Kong serves as the central layer for orchestrating microservices or conventional API traffic with ease. By centralizing common API functionality across all your organization’s services, the Kong API Gateway creates more freedom for engineering teams to focus on the challenges that matter most.
Cloudentity-Kong integration brings advanced authorization capabilities offered by Cloudentity to the distributed applications that are protected by the Kong API Gateway.
KongHQ offers two self-hosted versions of Kong Gateway: Enterprise and Open-source. Cloudentity provides a custom luarocks Cloudentity Kong Plugin that can be attached to the gateway in order to safeguard services deployed behind the Kong Gateway. Regardless of your choice, integration with Cloudentity and Kong Authorizer is seamless, as long as the authorizer and the plugin added to gateway can communicate. This applies whether your Kong Gateway is deployed via Docker container or Kubernetes using Helm Charts.
Integrate any Kong Gateway with Cloudentity using Kong Authorizer and the
kong-plugin-acp for enhanced access control, API discovery, and policy assignment.
Adding External Authorization to Kong Gateway
Services protected by Kong Authorizer lie behind the Kong Gateway. To safeguard a service, attach
the Cloudentity Kong Plugin, which contacts the /authorize endpoint of Kong
Authorizer and lets the authorizer discover Kong Gateway services. This enables authorization policy
assignment to chosen APIs.
When a client application with an access token from Cloudentity requests a protected service, Kong Gateway activates the Cloudentity Kong Plugin. This facilitates communication with Kong Authorizer to validate the request against the authorization policies for the specified API. On successful validation, the Kong Gateway processes the API request from the protected service.
Kong Gateway can be shielded using RBAC, Basic Auth, or OAuth 2.0 based on your Kong subscription and security preferences. More information can be found at Authenticating to the Kong Admin API.
Cloudentity Kong Plugin
Cloudentity Kong plugin is a LuaRocks plugin that is executed during the HTTP request/response lifecycle.
This plugin, in particular, is responsible for authorizing access to an upstream service. When you add the Cloudentity Kong plugin to your service, every request made by a client application to this service runs the plugin. The plugin assembles the request data and sends a query to Cloudentity’s Kong Authorizer that is responsible for comparing the request against an authorization policy defined for a given endpoint. After policy validation, the authorizer can respond whether the request should be allowed or denied.
AWS Authorizer
Amazon API Gateway is an Amazon Web Service (AWS) for creating, developing, publishing, maintaining, and monitoring stateless (REST and HTTP) and stateful (WebSocket) APIs. It allows the users to secure their APIs using built-in AWS features, but it also provides a possibility to delegate access control enforcement to external products that specialize in API protection such as Cloudentity.
Supported API Types
Cloudentity and its AWS API Gateway Lambda Authorizer supports access control for REST APIs.
In AWS API Gateway, you can delegate access control to the Cloudentity’s Amazon Gateway
Lambda Authorizer using Amazon’s API Gateway Lambda authorizers.
Lambda authorizers use lambda functions to control access to your APIs. When a client application
calls a method on the AWS Gateway, the gateway checks if the lambda authorizer is configured for the
method. If yes, it calls the lambda function. The Cloudentity’s Amazon
Gateway Lambda Authorizer is, in fact, a lambda function. It evaluates the result of the policy
assigned to the called method in Cloudentity and either grants access or denies it.
If access is denied the Amazon API Gateway returns the HTTP 403 ACCESS_DENIED status code.
If access is allowed, the gateway executes the method. The authorizer is also responsible for
pulling authorization policies definition from Cloudentity and providing
Cloudentity with a possibility to discover the APIs that have the authorizer attached.
For detailed information on how to integrate AWS API Gateway with Cloudentity, see Protecting APIs deployed behind the AWS API Gateway.
Azure Authorizer
Azure API Management is a hybrid, multicloud management platform for APIs across all environments.
Azure API Management helps customers meet these challenges:
- Abstract backend architecture diversity and complexity from API consumers
- Securely expose services hosted on and outside of Azure as APIs
- Protect, accelerate, and observe APIs
- Enable API discovery and consumption by internal and external users
For detailed information on how to integrate Azure API Gateways with Cloudentity, see Protecting APIs on Azure API Gateway.
Pyron Authorizer
Pyron is a lightweight, developers, and DevOps friendly API Gateway with advanced authentication and authorization capabilities. It’s build using Scala on top of the Vertx.io framework enabling high performance and non-blocking execution. Plugin based architecture allows further extensions of capabilities and features as well as seamless integrations. Native support of the HashiCorp Consul service catalog enables Pyron to bridge the traditional network with service discovery based routing. Support for declarative configuration model allows Pyron to be easily integrated into the CI/CD process.
For detailed information on how to integrate Pyron API Gateways with Cloudentity, see Protecting APIs on Azure API Gateway.
Multi-tenant Authorizers
Multi-tenant authorizer is an authorizer created in the system tenant, used to protect multi-tenant APIs in on-premise or private cloud deployments. You can create multiple system authorizers that protect different types of API gateways.
The solution for multiple-tenant authorizers consists of the following steps:
-
An authorizer is created in the system tenant.
-
The authorizer is deployed.
-
The services and APIs are synchronized only to the system tenant.
After the services and APIs are synchronized to the system tenant, the administrators of the client application tenant can create authorization policies and bind them to the system APIs. System services and APIs are read-only, so it is not possible for those administrators to change the services and APIs.
When an authorizer performs API enforcement, it fetches the configuration from Cloudentity, like available services, APIs, and their policies, for the specific tenant. It other words, there are two types of policies available. Those configured on the system tenant level, and those configured for a particular tenant.
Standalone Authorizer
The Standalone Authorizer provides a generic external authorization service for API gateways and applications.
The Standalone Authorizer is unique, because it is not specialized to any single product or technology, and is capable of serving in a variety of use-cases. This flexible option for external authorization, allows policy management for API access to be managed centrally, with benefits to visibility and auditability.
For detailed information on how to integrate AWS API Gateway with Cloudentity, see Protecting APIs deployed behind the AWS API Gateway.